Android Exploit: Force Factory Reset remotely
Android Exploit: Force Factory Reset remotely
"Android can be Exploited Remotely ". now just Clicking one wrong link can cause malicious code to execute, which could do anything Like infecting your computer with malware to wiping your phone data completely.
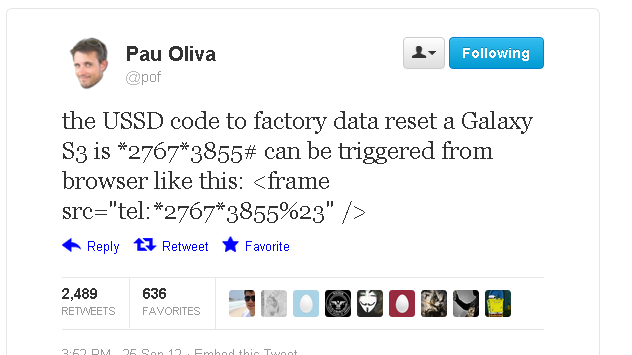
Researcher Ravi Borganokar demonstrated at the Ekoparty security conference in Argentina last week, that Only a single line of HTML code can be used to run a factory reset or even clear the SIM card on certain Samsung phones.
This code can trigger a full factory reset of Samsung’s best-selling Galaxy S3 smartphone, deleting contacts, photographs, music, apps and other valuable data. To Execute this code hackers just have to Inject code in a web page.
The devastating flaw lies in Samsung's dialling software, triggered by the tel protocol in a URL. It isn't applicable to all the company's Android handsets, but those that are vulnerable can take Precautions like Changing their PIN or is to disable automatic site loading in QR and NFC readers, and be careful about clicking potentially dodgy links or be wiped completely just by visiting a web page or snapping a bad QR code, or even bonking up against the wrong wireless NFC tag.
The tel protocol is generally used with phone numbers to provide clickable "call me" links on websites: tapping on the hyperlink in the handset's web browser opens up the dialling software and calls the number contained in the link.
For the time being, however, it appears that only Samsung phones running TouchWiz are susceptible (so not the Galaxy Nexus or any device running stock Android), and only if the malicious URL is loaded in the stock browser, rather than Chrome.


