Hacking Google users with Google's GooPass phishing attack

Hacking Google users with Google's GooPass phishing attack

Google Drive is the new home for Google Docs, that users can access everywhere for Storing files safely. In a recent demonstration hacker successfully performed an attack on Google Docs to trick users to grab their Facebook, Gmail, Yahoo credentials with Credit Card Information.
Security researcher Christy Philip Mathew came up with combination of Clickjacking and CSRF vulnerabilities in Google's Docs that can allow a hacker to create a document in victim's Drive for further phishing attack.
For those who are not aware about Clickjacking, It is a technique where an attacker tricks a user into performing certain actions on a website by hiding clickable elements inside an invisible iframe.
He explain how this technique can be executed to pwn a Google user to steal victim's all type of credentials with a phishing attack. Here attacker need to send a Malicious URL to the victim, where victim needs to interact with some buttons only.
Vulnerability allow hacker to trick Google user to create an document in victim's drive, which is actually owned by attacker and the victim. To perform a successful phishing attack, an attacker can carefully craft that document maliciously.
POC uploaded here and Demonstration Video as shown below:
After analyzing the possible threats of this vulnerability, I prepare an example for THN readers, where attacker can rename the document to something "Google GooPass" (imaginary service for storing passwords and important information secretly in Google drive) and crafted a simple design that can phish users to enter their Credit card information, Google, Facebook username password etc, as shown below:
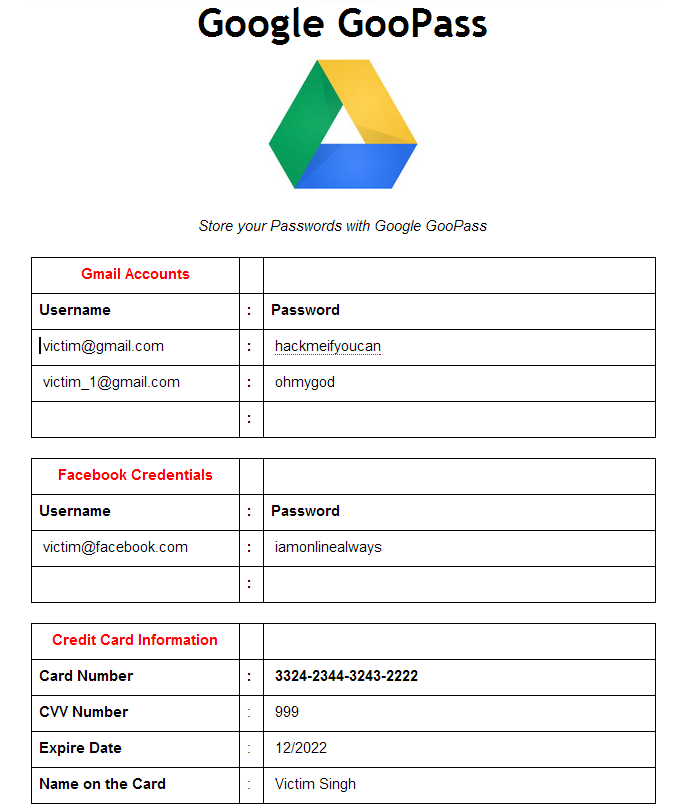
Victim can be led to believe that it's a Google default file or Service to save all type of personal information secretly at one location. Because attacker and victim, both are the owner of this new file, where attacker can make the document public for further access after removing himself from ownership of that document.
At the end, victim is only owner of the document (which is now public) and if phishing attempt works, hacker will be able to see all updates remotely, anytime - anywhere!
Note :
Vulnerability is not fixed yet, we urge Google to fix this as soon as possible to assure maximum security to Google users.
There is no Google service called 'Google GooPass', the term is just used to trick victim for phishing purpose.


