KRBanker Malware Targeting Korean Financial Institutions
KRBanker Malware Targeting Korean Financial Institutions
A recently discovered piece of malware called KRBanker (Korea + Banker = KRBanker) , targeting mostly online end-users at Korean financial institutions. According to nProtect, a global Internet and mobile security provider, during the initial stage of the attack by KRBanker, the malware infects the PC by attaching itself to Delphi and stops any antivirus software for keeping itself stealth into the system.
Then the malware pings back to the command and control (C&C) server with infection status and then the malware proceeds to download encrypted files on the victim’s PC.
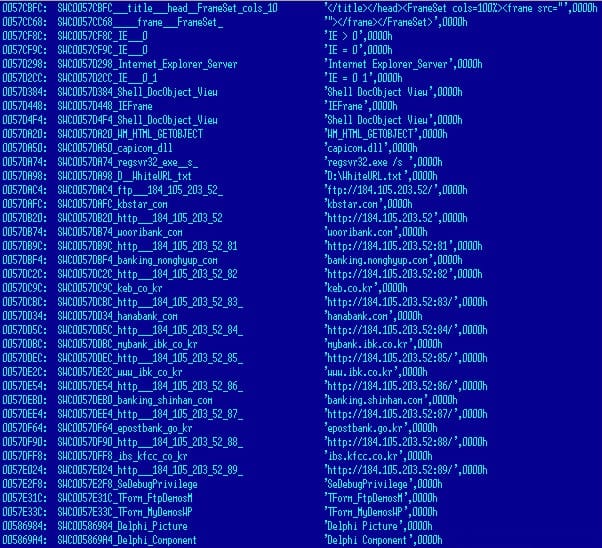
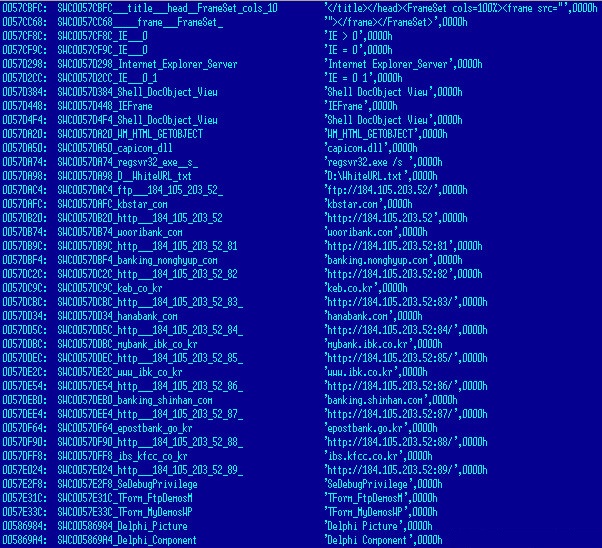
In the latest variant of the KRBanker malware, scans the PC for lists of DLLs that are related to Korean financial institutions, security software and patches any opcode instructions.
Malware instructed to insert the malicious code that will search and collect any information related to password, account details, and transaction history. Once logged, the compiled information is then sent to a remote server.
KRBanker will also collect digital certificates in the PC's NPKI directory. These unique digital certificates used both by individuals and corporate are normally used for all financial purposes such as banking, credit card, insurance, and more.
The hacker will collect digital certificates, password, account details, and screenshot information to gain fraudulent access to the victim's account.
After discovering KRBanker, which is distributed worldwide but concentrated mainly in Korea, nProtect Online Security quickly update their antivirus solution to defend against this malware.


