Major Flaw in Dirt Jumper Bot
Security Firm Reveals Flaw in Dirt Jumper Bot
A team of researchers has discovered a weakness in the command-and-control infrastructure of one of the major DDoS toolkits, Dirt Jumper, that enables them to stop attacks that are in progress.
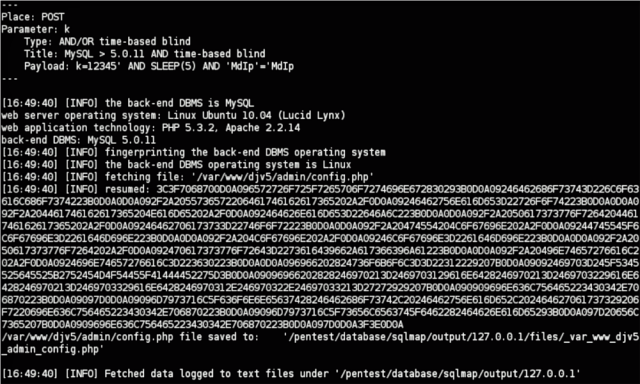
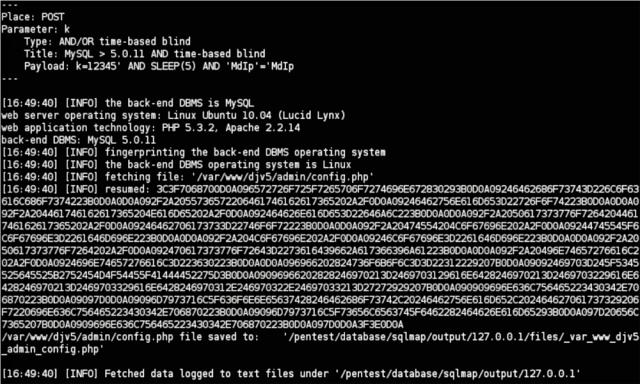
The command and control (C&C) servers of the Dirt Jumper DDoS toolkit can be compromised and, in principle, completely taken over via SQL injection holes.
SQL injection involves inserting database instructions in unexpected and unprotected places, effectively taking charge of a web application's database from the outside. According to the Prolexic report, the open source penetration testing tool sqlmap can be used to dump the contents of Dirt Jumper's database configuration file in a matter of seconds, revealing administrative usernames and passwords.
The company's research includes Dirt Jumper v.3, Pandora and Di BoT. According to Prolexic, the Dirt Jumper family of DDoS botnet kits was originally authored by an individual who uses the handle ‘sokol.’ Various versions of Dirt Jumper were sold privately and leaked to the public.
"DDoS attackers take pride in finding and exploiting weaknesses in the architecture and code of their targets. With this vulnerability report, we've turned the tables and exposed crucial weaknesses in their own tools," said Prolexic's CEO, Scott Hammack.
Pandora can be used to launch five different attack types, including a combination of techniques against the web application and infrastructure layers of targeted websites. Dirt Jumper seems to have overtaken rivals to become one of the most successful DDoS toolkits available on the Russian underground.
"Construction of a new variant of Dirt Jumper is relatively easy, only requiring basic knowledge of Delphi, a basic understanding of PHP and MySQL, and U.S. $5,000 to purchase the Dirt Jumper builder source code".


