Outdated version of WordPress leads to MasterCard Hack
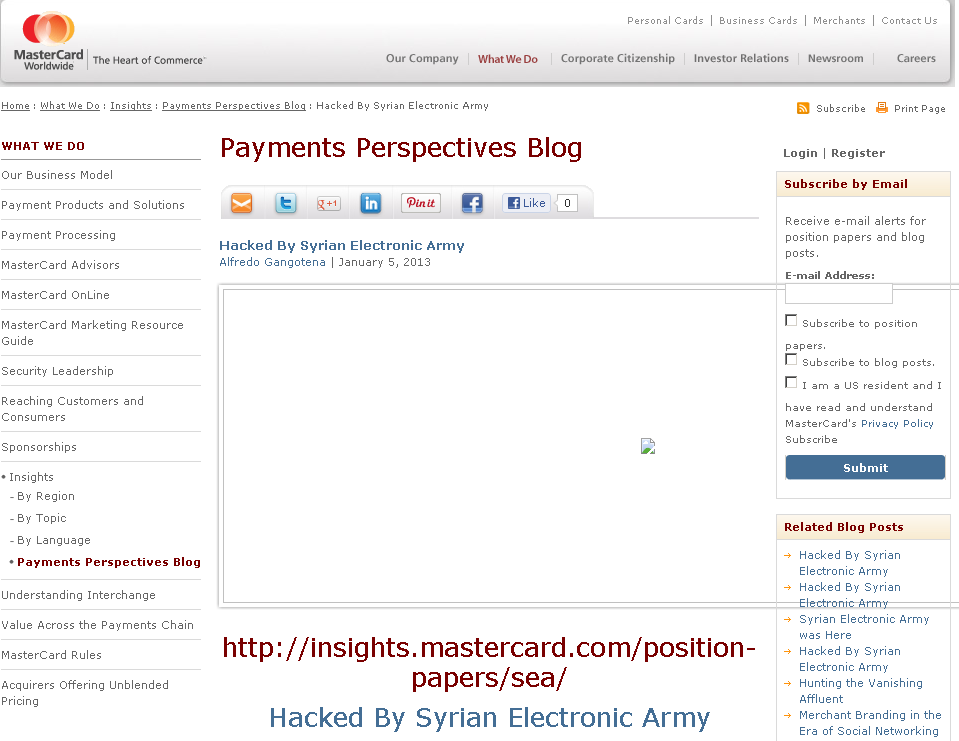
On tip of a readers, Few days back we came across a new MasterCard hack, performed by Syrian Electronic Army. Hackers was able to breach MasterCard Blog (https://insights.mastercard.com) and make a new blog post on the website with title "Hacked By Syrian Electronic Army" on January 5, 2013.
For now MasterCard deleted that post, but readers can check Google cache. Today we tried to contact the hacker, but may be they are busy in Hacking Next Target , I started my investigation that how they can hack such a big economic website's blog.
Starting from very first step, Information gathering about your target. Simple by reviewing the source code we found that MasterCard blog is using Wordpress. We all know, WordPress is particular a popular attack vector for cyber criminals.
To know this, I just tried to access the readme.html file of CMS , that's it - MasterCard #fail ! They are using an old Wordpress 3.3.2 version, instead of the current version 3.5 and Proudly vulnerable to many flaws like Cross Site scripting, File upload vulnerability, Cross-site request forgery (CSRF) etc.
As far I know, There is a good Cross-site request forgery (CSRF) exploit available on internet for Wordpress 3.3.2 Cross-site request forgery, that allow attacker to add a new admin user, using bit of social engineering with administrator.
Possibly Hacker may use any one of these vulnerability to hack MasterCard blog. WordPress and its plug-ins are always primary attack vectors for many attacks. You should always be using the latest version of your software, especially if you're a major company that is often targeted by hackers.
If you're also not using the latest version of WordPress, you should upgrade immediately.

