Wiper: The Destructive Malware
Wiper, the Destructive Malware possibly connected to Stuxnet and Duqu
Kaspersky Lab publishes research resulting from the digital forensic analysis of the hard disk images obtained from the machines attacked by the Wiper - a destructive malware program attacking computer systems related to oil facilities in Western Asia.
Security researchers from Kaspersky Lab have uncovered information suggesting a possible link between the mysterious malware that attacked Iranian oil ministry computers in April and the Stuxnet and Duqu cyber espionage threats.
The malware wipes data from hard drives, placing high priority on those with a .pnf extension, which are the type of files Stuxnet and Duqu used, and has other behavioral similarities, according to Schouwenberg.
It also deletes all traces of itself. As a result, researchers have not been able to get a sample, but they've reviewed mirror images left on hard drives. Kaspersky's researchers were not able to find the mysterious malware, which was given the name Wiper, because very little data from the affected hard disk drives was recoverable.
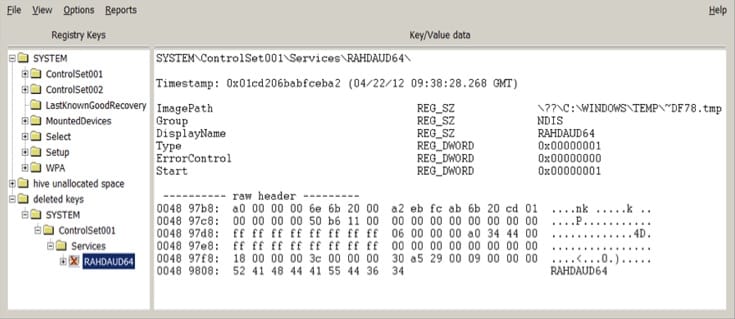
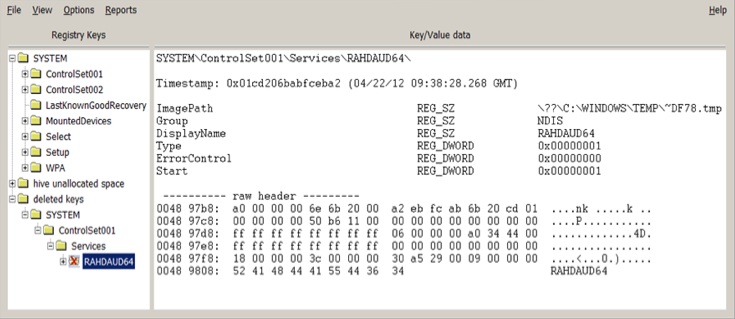
Even though a connection to Flame is unlikely, there is some evidence suggesting that Wiper might be related to Stuxnet or Duqu.For example, on a few of the hard drives analyzed, the researchers found traces of a service called RAHDAUD64 that loaded files named ~DFXX.tmp where XX are two random digits from the C:\WINDOWS\TEMP folder.
No one has ever found a sample of Wiper in order to study its code and determine exactly what it did to machines in Iran. According to Kaspersky, the malware’s algorithm is “designed to quickly destroy as many files as effectively as possible, which can include multiple gigabytes at a time.”
Although Flame can be updated by its creators with various modules, including conceivably a module that would destroy data, there has never been any evidence found that Flame had a module that was used to destroy data on machines or wipe out hard drives.


