In an alarming new discovery, cybersecurity experts have revealed a total of 19 vulnerabilities that will potentially impact millions of IoT (Internet of Things) devices around the globe. This flaw is apparently present in a particular library, which was designed back in the 1997. Since then, it has been extensively used and integrated in an endless list of IoT devices, spreading over both the industries and the consumer market.
IoT devices are simply hardware machines with a sensor that can be used to transmit data over the internet. These can include a number of products from satellite communication, data centers, power grids, healthcare medical machines, commercial aircrafts and other enterprise solutions to mobile phones, voice assistant devices like Google Home, Amazon Echo, etc. and Smart Home features are all equipped with IoT technology.
A look at the above range should give you an idea of the devastating impact this latest IoT vulnerability will pose. The newly-discovered 19 vulnerabilities were brought to light yesterday by CISA (Cybersecurity & Infrastructure Security Agency) ICS-CERT. These flaws have collectively been dubbed as ‘Ripple20’.
Ripple20 IoT Vulnerability: Introduction & Impact
Treck, a Cincinnati based software firm, developed a small TCP/ IP library about 20 years ago. This low level but essential software library became a part of many high-level hardware equipment directly, and was further integrated into several software suites indirectly. It’s main function is to connect the parent hardware or software to the internet via TCP/IP connections.
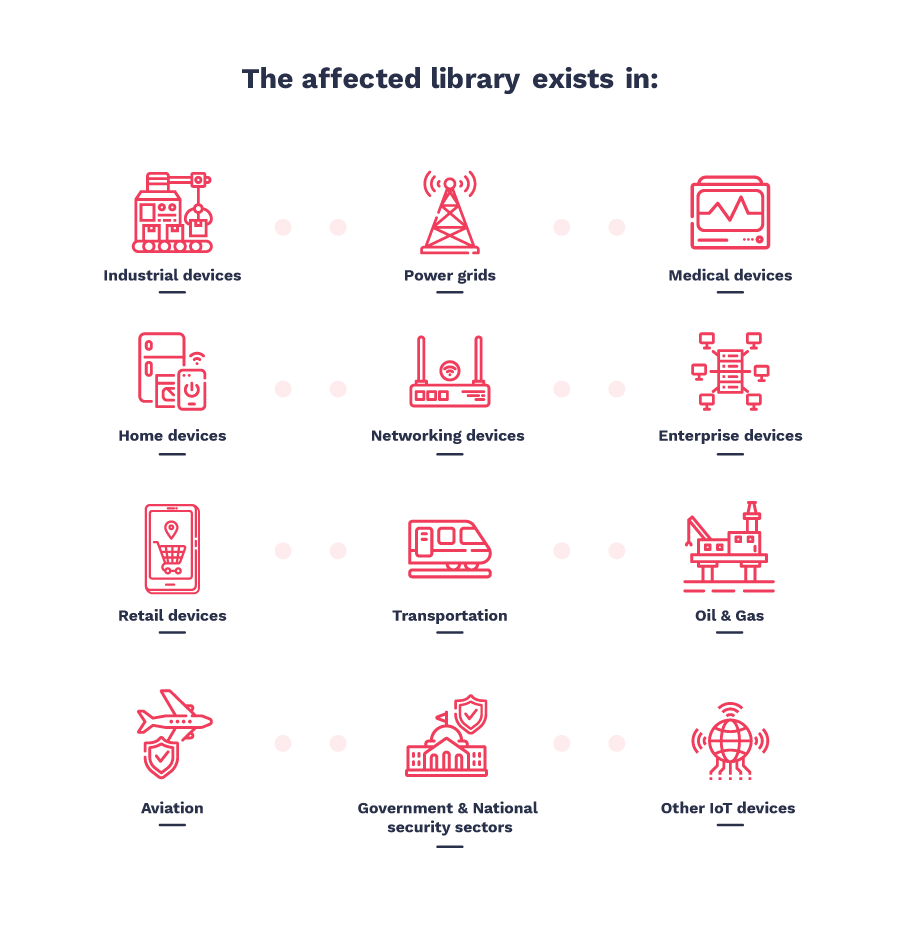
The Ripple20 vulnerabilities can be exploited to weaponize the target device by gaining full remote control, without the need of any user interaction. These flaws were first discovered by an Isreali cybersecurity firm, JSOF who started exploring Treck’s TCP/IP stack because of its vast reach and footprint across the globe. They have confirmed that during their research they found the affected devices to be widely used in following industries:
- Healthcare/ Medical
- Enterprises/ Data Centers
- Oil/ Gas
- Telecommunications/ Network
- Transportation (including Aircraft)
- Nuclear Plants
- And even in our Homes
Ripple20 got its name not from the number of vulnerabilities, but the year it got discovered in – 2020 and the ‘ripple’ effect it will have on IoT devices in years to come. JSOF added that this is only the beginning, and users should expect more discoveries to be made with respect to the Treck’s TCP/IP library. This especially applies to the list of devices that have the said library integrated in their system. As the research team can only cover so much ground, going forward, many vendors will have to check their own code.
Ripple20 Vulnerability: CVEs and Technical Details
Out of total 19 discovered Ripple20 vulnerabilities, few are so severe that the US Department of Homeland Security has scored them between 9.0 and 10 (on a scale of 1-10). The top rated and most devastating vulnerabilities of the pack can let the threat actor take complete control of the device remotely.
- CVE-2020-11896 - CVSSv3 Score: 10
Improper handling of length parameter inconsistency in IPv4/UDP component when handling a packet sent by an unauthorized network attacker. This vulnerability may result in remote code execution. - CVE-2020-11897 - CVSSv3 Score: 10
Improper handling of length parameter inconsistency in IPv6 component when handling a packet sent by an unauthorized network attacker. This vulnerability may result in possible out-of-bounds write. - CVE-2020-11898 - CVSSv3 Score: 9.8
Improper handling of length parameter inconsistency in IPv4/ICMPv4 component when handling a packet sent by an unauthorized network attacker. This vulnerability may result in exposure of sensitive information. - CVE-2020-11899 - CVSSv3 Score: 9.8
Improper input validation in IPv6 component when handling a packet sent by an unauthorized network attacker. This vulnerability may allow exposure of sensitive information. - CVE-2020-11900 - CVSSv3 Score: 9.3
Possible double free in IPv4 tunneling component when handling a packet sent by a network attacker. This vulnerability may result in remote code execution. - CVE-2020-11901 - CVSSv3 Score: 9.0
Improper input validation in the DNS resolver component when handling a packet sent by an unauthorized network attacker. This vulnerability may result in remote code execution.
Like mentioned before, these high-severity vulnerabilities can be weaponized to takeover on any industrial-level or home/ personal smart device. These attacks can be launched via:
- Internet - If the target device is connected to one
- Local Network - Like a compromised router
However, rest of the Ripple20 vulnerabilities have been rated from 3.1 to 8.2 CVSS score, can cause multitude effects such as Denial of Service to potential Remote Code Execution.
Another interesting fact uncovered is that apart from single-device exploits, Ripple20 can also be used for botnet attack. Let’s watch a demonstration from JSOF to understand this exploit better.
Ripple20 Patch, Affected Devices and Future Steps
JSOF team’s research uncovered major vulnerabilities, and they have been collaborating with national CERT (Computer Emergency Response Teams) departments in various countries to patch the issues.
Moreover, over the years, some of Ripple20 flaws were fixed by Treck and machine manufacturers due to stack configurability and code changes. Because of the very same reason, some of Ripple20 flaws now have variants. For this, manufacturers and vendors will have to perform an extensive risk assessment as in most cases the vulnerable library might not even appear in the product’s code manifests.
The JSOF team has taken vital steps from the beginning of their research to keep everyone informed and close the vulnerabilities successfully. They brought Treck on board very early on, working with them to analyze the vulnerabilities and fixing the issues. Next step was finding the affected equipment and reaching out to the respective vendors. Around 500 vendors have already been updated about the situation, with some acknowledging the fault and others who are still assessing their products.
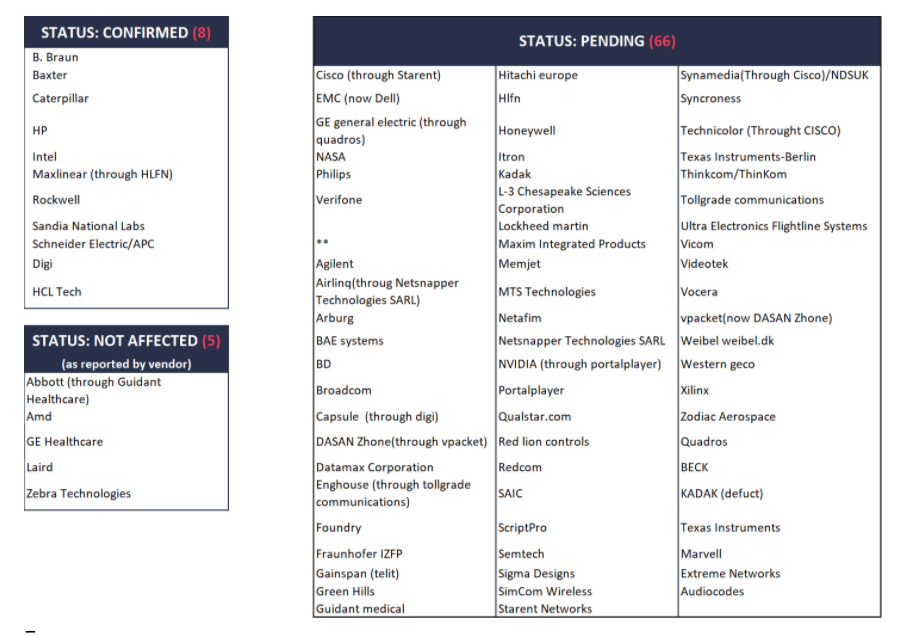
Fortunately, Treck has confirmed that all Ripple20 vulnerabilities have been patched and available for concerned parties. Furthermore, Treck has also fixed most of Ripple20 identified issues in its latest release TCP/IP stack version 6.0.1.67 or higher.
As reported above, Ripple20 affects millions and millions of devices worldwide, and the possibility of everyone getting the patch on time is slim. So in the meanwhile, we should follow the US-CERT advice to:
- For all control system devices, minimize their network exposure by cutting them off from the internet.
- Keep control system networks and remote devices behind firewalls, and isolate them from the business network.
- Use secure methods such as VPNs for acquiring remote access.
- Use an internal DNS server that performs DNS-over-HTTPS for lookups.
To read the full length report by the JSOF team click here.
To read the CISA US-CERT announcement, click here.
Follow us on Telegram and Twitter for all such latest cybersecurity news and updates.







