7 Thunderbolt Vulnerabilities Affect Millions of Devices: 'Thunderspy' Allows Physical Hacking in 5 Minutes
Do you own a Thunderbolt equipped laptop, and have bought it after 2011? Well, we’ve news for YOU. 7 newly discovered Intel Thunderbolt vulnerabilities have exposed your device to hackers. Learn what to do?

How many times have you heard the advice “Don’t leave your laptop unattended” and didn’t really follow through. Turns out, the warnings were right all along, and referred to circumstances like this. In a shocking new tech-news, a Dutch researcher has come through and demonstrated how a hacker can gain full access to your computer in mere 5 minutes.
His research is based on Thunderbolt, a hardware interface developed by Intel and Apple, which has now become the center of attention with several fresh vulnerabilities coming to light. To detail, Thunderbolt is an advanced technology that provides high performance data and displays through a single port. It provides DC power, Display Ports and PCI Express all in one cable for easier management. Most commonly seen in Apple Macs, Windows, and possibly every other currently in-use laptop/ desktops.

But on May 10, 2020, Björn Ruytenberg, a dutch researcher from Eindhoven University of Technology reported his study on multiple Thunderbolt flaws and how they can be exploited. His research includes 7 unpatchable hardware vulnerabilities and 9 attack methods, which are collectively called ‘Thunderspy’. As obvious the target device must have a Thunderbolt port, and must be physically accessible for the threat actor. Ruytenberg came up with multiple distinct, practical scenarios on how to hack a PC using Thunderbolt.
The attack works by gaining read/ write permissions of the system's storage, and eventually accessing all available data. The scariest part is that this hack is not dependent on logging in the system; contrary to popular belief here the infiltration can happen on locked out, or even sleeping computers, bypassing Intel’s high security design and parameters. No system security best practices like OS passwords, secure boot, robust BIOS or disk encryption can save you.
Now let’s dive deep into how Ruytenberg approached the subject, and break down all his findings:
Thunderbolt Vulnerabilities – How Thunderspy Hack Works?
Vulnerable Thunderbolt Versions: ALL (1, 2 and 3)
Vulnerable models include all laptops and desktop machines manufactured between 2011 to 2019, specifically:
- Windows
- Linux
- Macs:
- Fully vulnerable when running Bootcamp
- Partially vulnerable with MacOS (excluding Retina MacBooks)
Thunderspy performs an “Evil Maid Attack”, where an unattended device is accessed/ exploited/ altered through physical access, but the act in itself remains undetectable. The reference to the name comes from an instance of a spy in maid’s costume committing corporate espionage, as explained by the Polish researcher, Joanna Rutkowska.
As is clear from the example above, Thunderspy leaves no evidence of intrusion and can be executed in as fast as 5 minutes. To get a better understanding, let’s take a look at the 7 Thunderspy Vulnerabilities listed by Ruytenberg and his Eindhoven team:
- Inadequate firmware verification schemes
- Weak device authentication scheme
- Use of unauthenticated device metadata
- Downgrade attack using backwards compatibility
- Use of unauthenticated controller configurations
- SPI flash interface deficiencies
- No Thunderbolt security on Boot Camp
Thunderspy exploits your computer through Direct Memory Access (or DMA) attacks. To do this, it creates ‘arbitrary Thunderbolt identities’ and clones ‘user authorized Thunderbolt devices’, to achieve the end-goal of acquiring PCIe (Peripheral Component Interconnect Express) control for DMA attacks.
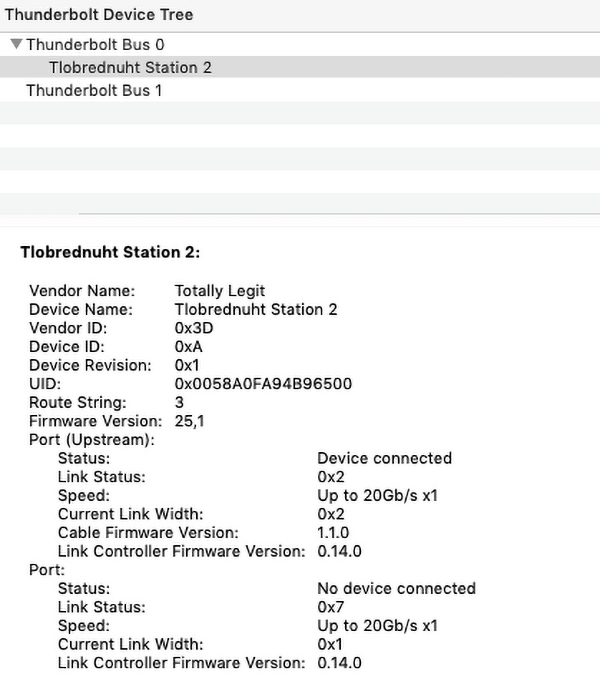
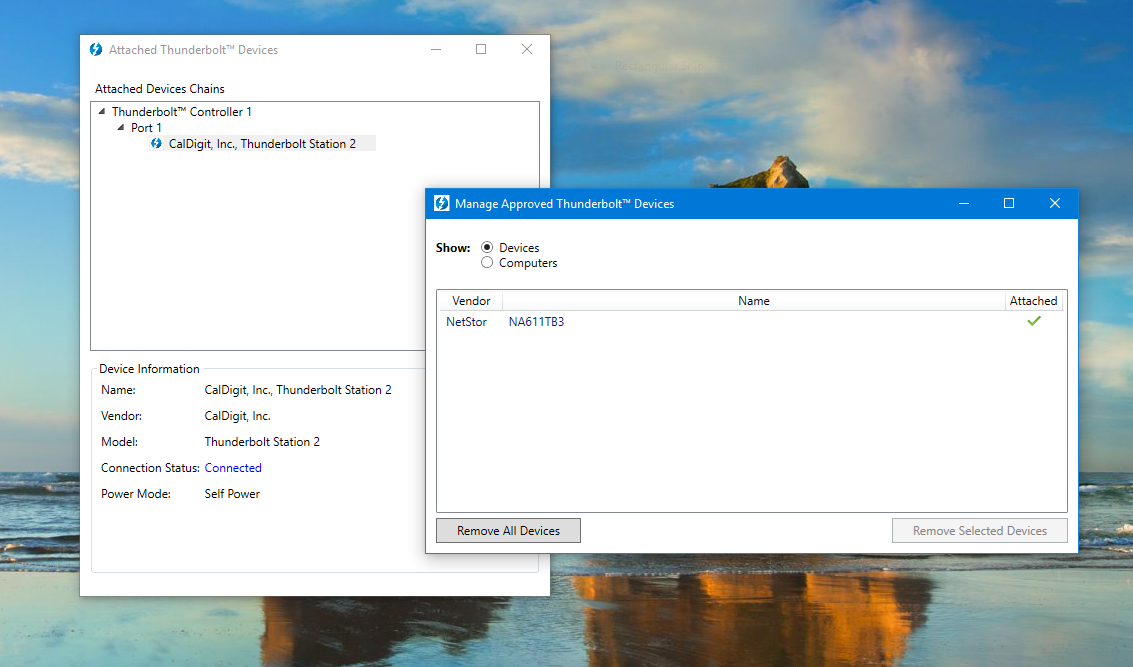
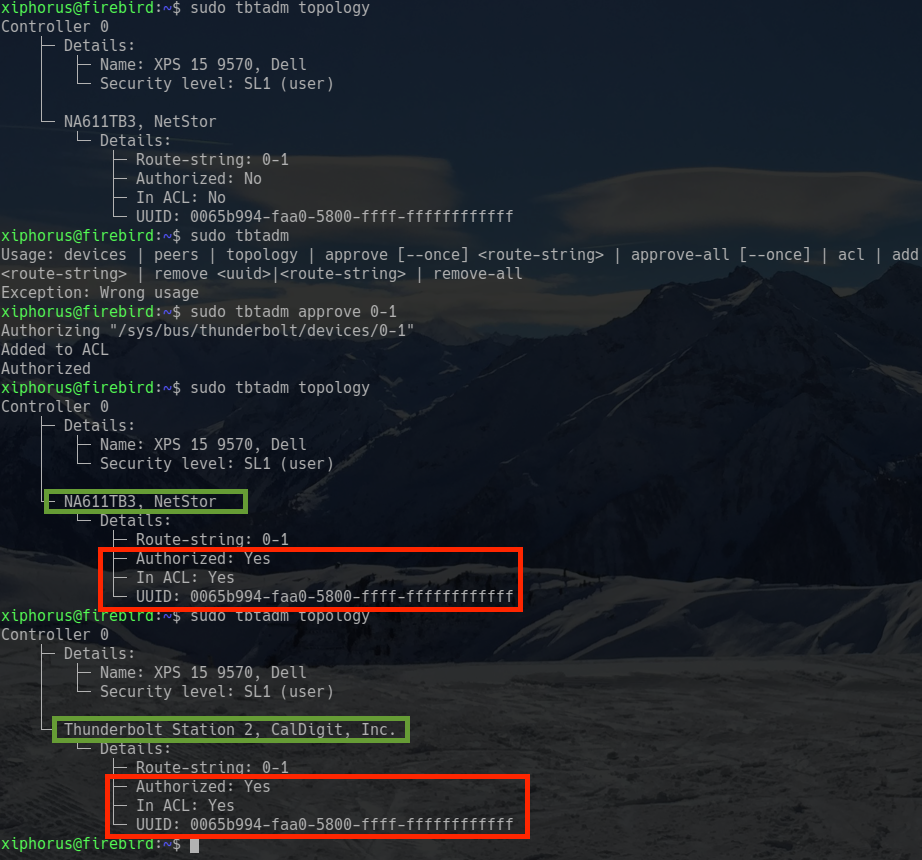
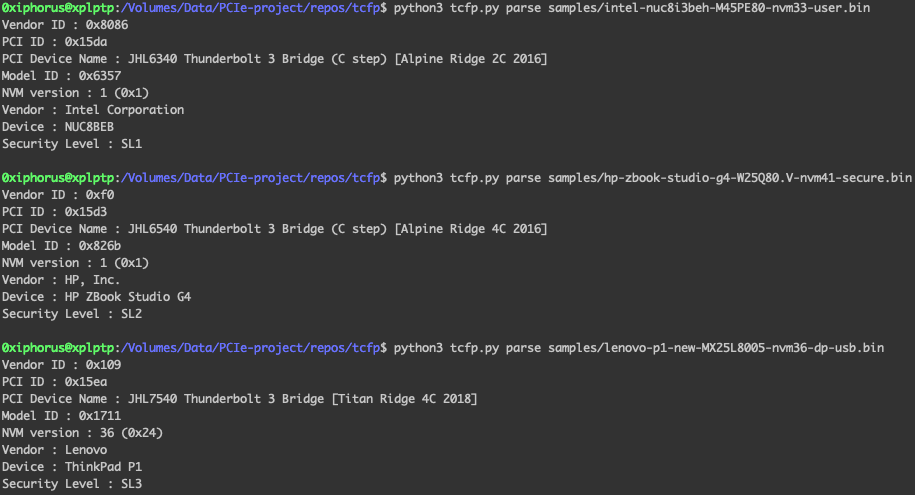
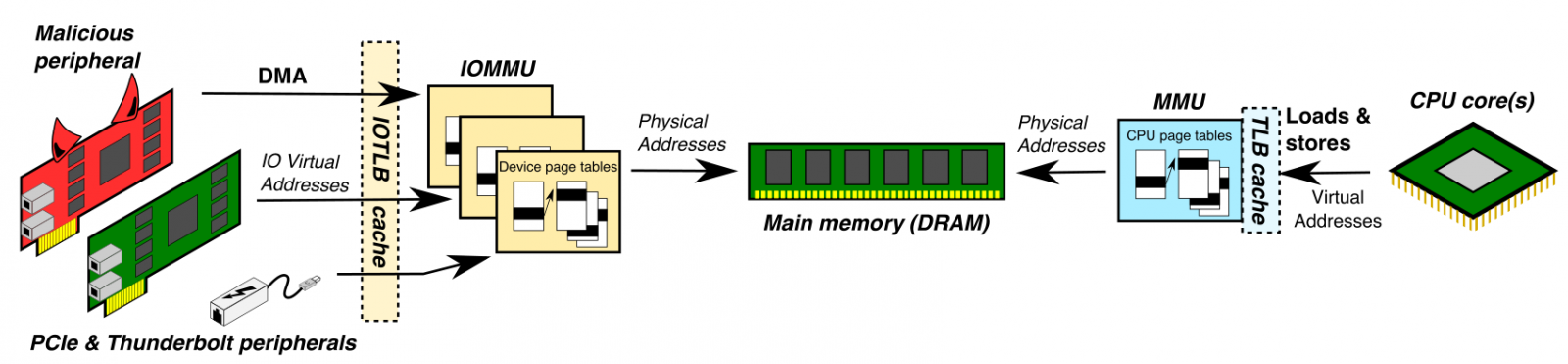
But how does a single Thunderbolt port provide this high privilege access?
How Was Thunderbolt Hacked? – It’s Long Suspected Security Risks
In spite of its wide use and popularity, Thunderbolt’s interface and working has been a point of concern for many security experts. Thunderbolt, no doubt, provides exceptional transfer speed, but in doing so, it opens a direct and wider access channel to the computer’s memory.
A similar research paper by the name of “Thunderclap” was rolled out in February, 2019, demonstrating the adverse-side of Thunderbolt. The study shed light on how plugging a malicious hot plug accessory into this port allowed hackers to control any PC remotely.
For defence against Thunderclap, researchers suggested turning off Thunderbolt or restricting access to untrusted devices. This was managed in the ‘security levels’ of the OS settings, and would alter the Thunderbolt into a simple USB and display port.
But Björn Ruytenberg’s method goes a step above and beyond to circumvent these updated settings. Instead of focusing on the high-level security, Thunderspy instead goes straight for the internal firmware and modifies the permissions to ‘allow access to any device’. To simplify, Thunderbolt allows peripherals to bypass OS security, and grants access to read/ write computer memory, which also contains sensitive files, passwords, banking logins, etc. Furthermore, Ruytenberg found a way to disable ‘Thunderbolt security and future firmware updates’.
After the Thunderclap research last year, Intel jumped in with a new security update ‘Kernel Direct Memory Access Protection’. This powerful layer gives additional protection against attacks like ‘Thunderspy’ as well. But a lot of Thunderbolts manufactured before KDMA Protection release are not compatible with this, so all devices shipped before 2019 (and some after) are still vulnerable to the 7 Thunderspy flaws. Here’s few brand names (manufactured since 2019) that are said to not be affected by ThunderSpy and provide protection against DMA attacks:
- Windows 10, 1803
- MacOS Sierra 10.12.4
- Linux kernel 5.x
- HP EliteBook and ZBook 2019 (with internal PCI card)
- Lenovo ThinkPad P53, X1 Carbon 2019, Yoga C940 (w/ Ice Lake CPU)
How to Fix Thunderbolt Vulnerability – Is there a Thunderspy Patch?
Thunderspy vulnerability has been announced to the world just now, and the security experts are still assessing the threat, its global impact and approach on how to fix it.
Intel and other major players in the tech hardware industry have not provided any conclusive statements till now. Since Thunderspy vulnerability is a hardware flaw, hence it is unpatchable for the machines already with customers and in markets. Unlike other other tech vulnerabilities, this can’t be fixed with a simple software update, or even by manually updating your Thunderbolt/ OS settings. Ruytenberg clarifies the ultimate fix will require a silicon redesign.
During multiple reports of this case, it was revealed that Intel was aware of Thunderbolt 1 and 2’s vulnerabilities but never intended to disclose it to the public officially. But the company assured that they will gear future Thundebolt versions with advanced hardware protection.
For anyone who owns a Thunderbolt enabled laptop/ desktop purchased between 2011 to 2019 (honestly, that’s 90% of us), here’s few steps you can follow to safeguard your system against Thunderspy hands-on hacks:
- You can start by following chapter 101 from computer security class:
- Never leave your machine unattended, or
- If need be, shut it off completely, or
- At least put it in hibernation mode instead of sleep - Don’t connect any untrusted devices to your thunderbolt port
- Connect only your own peripheral devices and never lend them to any suspicious character
- Disable your Thunderbolt port in the system BIOS
- Enable hard disk encryption
- For additional assurance, you can verify if your system is vulnerable to Thunderspy attacks or not. For this, Ruytenberg has developed an open source tool by the name of Spycheck. If found vulnerable, Spycheck will also advise users for system protection:
- Click here for Windows
- Click here on Linux
We cannot close the commentary on Thunderspy without acknowledging and commending the valuable research from Ruytenberg and his Eindhoven university team. Their intensive exploration on Thundebolt might just have saved hundreds of sensitive information in the times to come. They are currently working on finding more potential vulnerabilities and will launch them soon in the next case study ‘Thunderspy 2’.
The Dutch researcher also plans to officially present his research material at the Black Hat security conference (to be held virtually this year). To read their full white paper on the subject, click here.


