‘BHIM’ App Data Leak Exposes 7M Indian Users Sensitive Data – Risk of Financial Fraud, Identity Theft
Indian E-Payments/ UPI App ‘BHIM’ data breach includes high value citizen information like copies of Aadhaar Card and PAN Card, Bank and Biometric details, Contact information and more personal data.

Data Breaches have become as frequent as an influencer’s Instagram posts. This week’s most alarming data breach news comes to us from the Indian E-Payments and UPI mobile application - BHIM (Bharat Interface for Money).
BHIM is a government sponsored payments application, developed by CSC (Common Service Centres Scheme) E-governance Services Ltd. Launched in 2016 by NCPI (National Payments Corporation of India), the app boasts of over 136 Million downloads. In Addition, the app works on the UPI technology, that stands for Unified Payments Interface that enables financial transactions by assigning unique IDs to users. Interestingly UPI project is also developed by NCPI.
An authorized app, like BHIM, is highly trusted by users when jumping onto a new technology, especially in the financial zone. BHIM was heavily marketed by the Indian government during the 2016 demonetisation phase for easy and instant money transfers. That’s why the BHIM hacking news comes as such a shock, (looking into the app’s background and it’s direct support from the government).
The news was first reported on May 30th, 2020 by VPNMentor, a cybersecurity firm, who discovered the breach back on April 23rd, 2020 and notified the BHIM team and CERT-In (Computer Emergency Response Team) in time. Let’s take a deep look at the report to understand what got leaked and how it could affect the registered BHIM users.
BHIM Data Leak Details
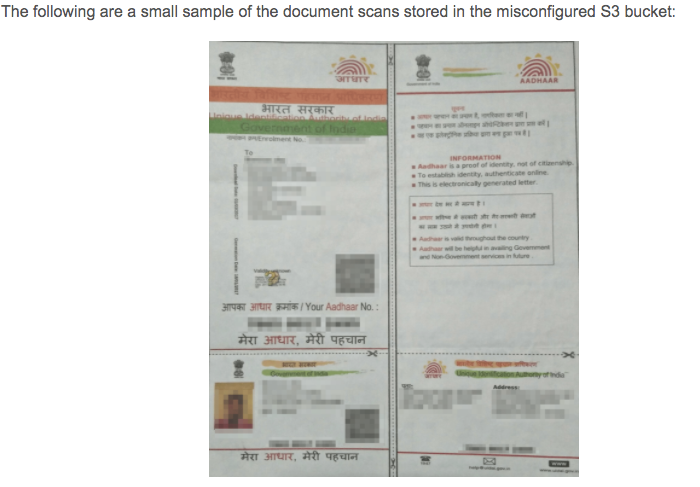
The BHIM data dump exposed during this breach amounted to 409 GB with approximately 7.26 Million Indian user records. The individuals ranged from all backgrounds, age groups (including minors), religions and status. The leaked files are highly confidential, with sensitive details like Personal Identifiable Information (PII) and financial information. This further consisted of complete user profiles and corresponding banking records, with specifics like:
- Name
- Age
- Gender
- Date of Birth
- Address
- Profile and ID Pictures
- Religion and Caste Status
- Fingerprint scans
- Scanned Copies of
- Aadhaar Card (National ID of India)
- PAN (Permanent Account Number) Card (by Indian Income Tax Department)
- Caste Certificates
- Proof of Residence
- Educational and Professional Certificates - ID numbers for
- Government Programs
- Social Security Services - Screencaps of financial transactions within banking apps, stored as proof
- Business Names and respective UPI IDs
- And more



How the BHIM Data Breach Happened?
The source of the breach was CSC BHIM website - http://cscbhim.in/, that was “used in a campaign to sign large numbers of users and business merchants to the app” across all states of India. The data from this campaign was stored on the widely-used Amazon Web Services S3 bucket, which was ‘not secure’ due to a developer’s carelessness. This would be technically referred to as AWS S3 bucket misconfiguration.
S3 buckets is a cloud storage facility that is one of the most used and preferred choices throughout the globe. But while integration, the developer needs to follow security best practices and set up certain protocols, suitable for their environment.
The exposed BHIM data was available in the S3 bucket, labeled as ‘csc-bhim’. It held the PII and financial data for a huge number of individuals and businesses who signed up for the said campaign, like:
- Farmers
- Mechanics
- Service Providers
- Store Owners
- And more
BHIM Hacking Devastating Impacts
This massive breach has left millions of Indian citizens in shock and worried for their privacy, and rightly so. With the amount of public data at stake, it has become a deeply concerning issue, which will lead up to various fraudulent activities and damaging long-term impact.
One of the major leaks in the BHIM hacking is the UPI IDs. UPI payment system is an alternate approach for financial transactions. You can consider it equivalent to a bank account. This makes the BHIM UPI data like a goldmine for hackers and cybercriminals, who can utilize these, in combination with PII, for various illegal transactions like:
- Identity Theft
- Tax Fraud
- E-Payment Theft
- Phishing Attacks
Moreover, the exposed S3 bucket also contained an APK (Android Application Package), which is a private file used by Android OS while app installation. Noam Rotem and Ran Locar, the lead researchers from VPNMentor explain,
“AWS Key pairs are the equivalent of admin user/password in Amazon’s infrastructure, potentially giving the holder of the key access to all data, the ability to start and stop servers, access the S3 bucket’s controls, and more. We did not test the credentials, but even their presence is an alarming sign of bad security design practices.”
India being a development company, most of its population is either uneducated or unaware of how scams work. They can be the perfect audience for a cyber attacker, trying to leverage this opportunity. This extensive exposure of private data will also create a difference and trust shift between the “Indian public, government bodies, and technology companies”.
Official Statement on ‘BHIM Hacked’
Interestingly, BHIM and NCPI have both denied any possibility of this data breach, stating that,
“We have come across some news reports which suggest data breach at BHIM App. We would like to clarify that there has been no data compromise at BHIM App and request everyone to not fall prey to such speculations. NPCI follows a high level of security and an integrated approach to protect its infrastructure and continue to provide a robust payments ecosystem”
Next Steps on BHIM Data Breach
As per VPNMentor report, the BHIM data breach was patched on May 22nd, 2020. Even if the case is closed, the data might still be out there, as a threat actor could have accessed it during the one year (allegedly) that it was open for.
But this is definitely not the last of data breach or ransomware infiltration. Users should be educated and aware about how to protect their data. Let’s quickly go through some efficient tips:
- Change your password often, specially after a data breach news, to a strong alpha-numeric key
- Never share your OTP with any stranger, even anyone posing from the bank or government sector
- Don’t share your bank/ card details with anyone over the phone, messages or emails
- Don’t click on any suspicious link in an email, or fill out your personal information
- Never install untrusted applications
- Lastly, if you’re highly concerned, you can directly get in touch with CSC e-Governance Services and enquire about the issue and their next steps
Stay Updated, Stay Safe!


