Firebase Misconfiguration Exposes 24000+ Android Apps’ Sensitive User Data
Alert for all Android phone users & App developers: Researchers have discovered the latest data breach possibility via Google Firebase, that is allowing major data leaks like user passwords, contact details and more. Learn how to fix misconfigured Firebase.

Google owned and operated Firebase is undoubtedly the most trusted production platform, especially by Mobile App developers. Launched in 2011, it quickly made its place in the tech world because of its comprehensive list of services, all under one roof. Some of its popularly sought after features include,
- Serverless App Development
- Cross-platform collaboration
- Real-time Database Management
- Cloud Storage
- App Hosting
- Crashlytics
- User Authentication
- Remote Configuration
- Push Notifications and much more

As one of the most reliable Android App Databases and focused on user-security, Firebase is currently associated with more than 30% of the Google Play Store Apps. But like every other development software, configuration is the key here as well. This statement has now been validated by Comparitech, a tech research firm, when they introduced the latest Firebase database exploit involving misconfiguration.
On May 11, 2020, Comparitech, disclosed their investigative research on Android apps security, stating that some common Google Firebase Misconfigurations allow unauthorized access to user-personal data. Approximately 24,000 Android apps have been exposed, with abundant data dump available for anyone who knows where to look.
Firebase Database Android Apps Exposed - Behind the Research
The team responsible for this breakthrough research was led by Bob Diachenko. In the time available, they were able to examine a small pool of applications, from the vast Google Play Store ocean. For a clearer insight, we’re breaking down their research specifics and findings below:
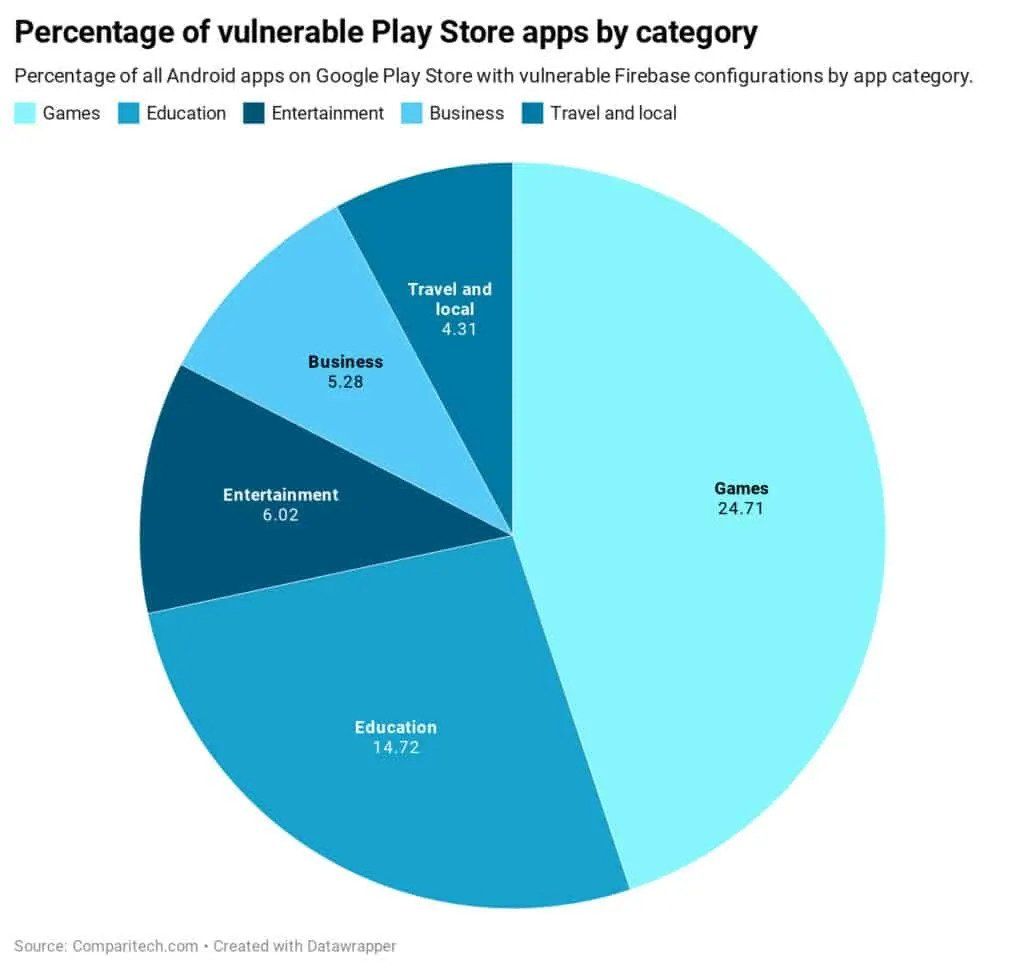
- The team studied 515,735 applications, which comprises only 18% of the total available apps on the Google Play Store channel
- Out of them, 155,066 apps were using Firebase services
- Next, around 11,730 were publicly exposing their Firebase database
- Particularly 9,014 apps contained the ‘write’ authorization, where hackers can add, edit, delete, download the information
- More in-depth analysis revealed, that 4,282 Android applications were leaking sensitive data
- Comparitech further extrapolated these numbers to give us an idea of vulnerability’s vastness:
- Going by 4,282 out of 515,735 apps ratio, we get 0.8-0.9% of all Google Play Store Apps.
- That somewhere amounts to 24,000 Android Apps that are potentially exposed to Firebase misconfiguration error
As per Firebase’s official records, it is estimated that currently over 1.5 million apps across iOS and Android are using this database and related utilities. Comparitech revealed that the confirmed vulnerable applications have 4.22 billion downloads. Given such high stakes, the Firebase hack must be taken seriously.
Firebase Misconfiguration Error - Analysis & Discoveries
Comparitech revealed the process that led them to this valuable piece of discovery. Their initial approach included sorting the Apps using Firebase by searching the text strings in the app resources. Another troubling matter here is that Firebase database urls are normally indexed on SEs like Bing. Next came the simplest and most important step – Append .json at the end of Firebase URL. Ideally the result on this hit should be ‘Access Denied’, but as established above, the researchers got many positive results. From there on, they manually examined the databases for any sensitive information.
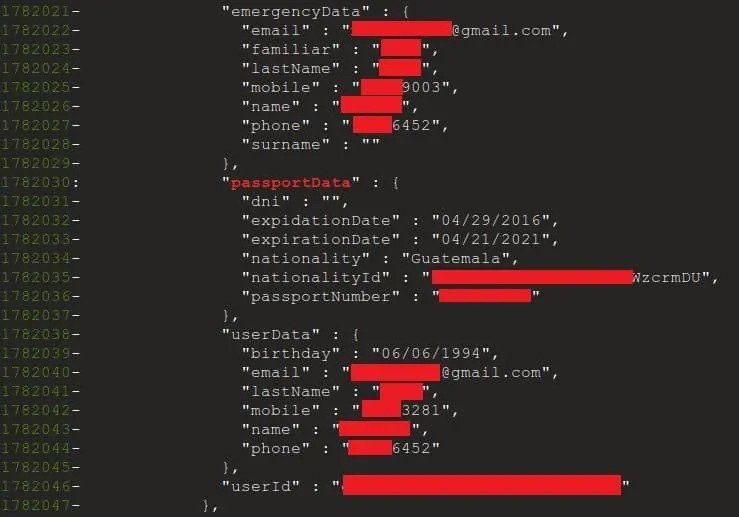
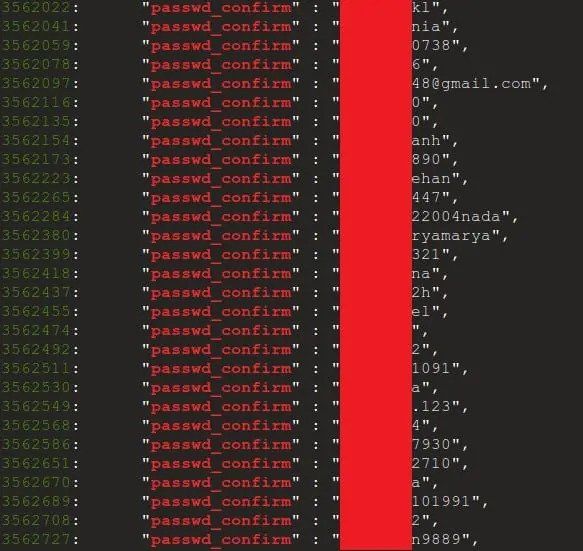
The investigating team has assured of their White Hat techniques, confirming that they destroyed all data that was discovered and accessed for research purposes. The exposed data unveiled the following statistics:
- 7,000,000+ Email IDs
- 4,400,000+ Usernames
- 1,000,000+ Passwords
- 5,300,000+ Contact Numbers
- 18,300,000+ Names
- 6,800,000+ Messages
- 6,200,000+ GPS Location
- 156,000+ IP Addresses
- 560,000+ Physical Addresses
- Credit Cards information
- Official Identity Proof’s information and much more
How to Fix Firebase Misconfiguration Issues?
Following the discovery, Google Firebase ‘security’ is surrounded by many questions and speculations. Is Firebase secure? Can you bypass Firebase?
But lo and behold, it isn’t quite Google Firebase’s flaw, but rather a development-side fault. That being said, such misconfiguration issues are quite common within databases, and have a complex history of how that came to be. Earlier in 2020, reports suggested that around 82% of cybersecurity related vulnerabilities were credited to some sort of misconfiguration errors.
Coming back to the Firebase Misconfiguration issue, you should be aware of the next-level threats that this error may cause. If an attacker gets access to your database, then exploiting insecure firebase for malicious data and malware would be easy as pie.
Rather than making it a blame-game, if you’re an App owner/ developer, you should look forward to the below mentioned preventive and resolving measures:
- First and foremost, Comparitech has strongly recommended all Firebase equipped app developers to check up on their configuration settings instantly.
- Implement conventional database rules, and pay keen attention to restrict unauthorized access to databases.
- All app developers must create a checklist and follow Google Firebase’s official Security guidelines documentation.
- Since this is a misconfiguration issue, and a lot of developers might come under scrutiny because of it, we want to raise a point in their favor. During development and project delivery, ‘Time Pressure’ is a huge issue, because of which certain instructions might be neglected. Proper timeline must be given for adequate and smooth evolution of the project.
- This research was only carried out for Android applications, but it applies to anyone using Firebase database. If you do, it’s high time to check your Firebase security and permission levels.
- For all app users, as a general practice you must only provide sensitive and personal information to trusted applications.
The Comparitech team informed Google their report findings on April 22, 2020, prior to publishing it publicly. Google gave the following response:
"Firebase provides a number of features that help our developers configure their deployments securely. We provide notifications to developers about potential misconfigurations in their deployments and offer recommendations for correcting them. We are reaching out to affected developers to help them address these issues."
Interested in reading the full report by Comparitech? Click here.


