Critical SaltStack Vulnerability Gives Hackers Root Access to Cloud Servers & Data Centers
Salt’s users are under huge threat because of 2 recently-found high-severity RCE (remote code execution) vulnerabilities. Big Names like LineageOS, Ghost, DataCert have also been affected by the exploit.

2020 is really something! We’re not even halfway through and the world is collectively suffering from world war threats to pandemics. And with the internet consuming most part of our lives, how can the digital scares be far behind? Though regular hacking news, and cyberattacks have become a daily read, we’ve just been hit by a huge cyber-storm that will potentially affect thousands of businesses.
SaltStack has been hacked! The Salt management software is widely used to manage data centers and cloud servers by many popular enterprises like LinkedIn, eBay, IBM, Fiserv, Ericsson, Lego, Dish and others. On April 30th, 2020 F-Secure, a cybersecurity firm, released their latest discovery involving the Salt configuration tool. They have warned that Salt’s users are under huge threat because of 2 recently-found high-severity RCE (remote code execution) vulnerabilities.
The tracked vulnerabilities have been allocated the ids CVE-2020-11651 and CVE-2020-11652, with CVSS (common vulnerability scoring system) score reaching upto 10, deeming it as extremely critical and sensitive.
The team behind this research has denied the POC (proof-of-concept) exploit stating the high risk factor “due to reliability and simplicity of exploitation”. But we can still take you through the process of ‘what, why and how’ of these critical Salt vulnerabilities.
Salt RCE Exploit - How it Works?
The Salt project has been termed as the “heart” of SaltStack organization. It’s basic service is to monitor and update servers in data centers and cloud environments.
Background – Master, Minion, ZeroMQ
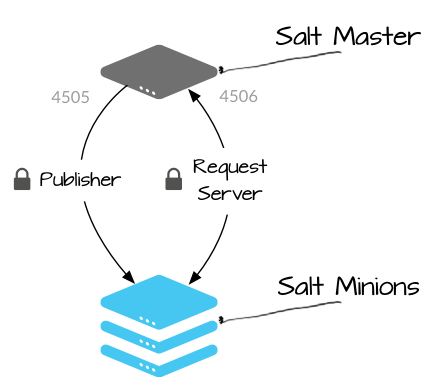
The framework’s internal architecture works on a ‘minion’ (a server agent) and ‘master’ (software installation) concept. ‘Master’ publishes updates such as software and configuration messages for the minions, which in turn connect and give their state reports to the master node. Interestingly, master commands can also be deployed to multiple managed ‘minion’ servers asynchronously.
This master-slave communication is handled by Salt’s default communication library ‘ZeroMQ’. It further works on 2 channels ‘request server’ and ‘publish server’ – Here the minions connect to the ‘request server’ channel to report their output status, and the master publishes its commands on ‘publish server’ channel for the minions to act on.
1. CVE-2020-11651 Vulnerability Explained
An unintentional authentication bypass due to a salt-master process, namely ‘ClearFuncs’. This class is unable to validate method calls and exposes: _send_pub() and _prep_auth_info().
Effect: Allows any remote unauthenticated user to access above methods, which in turn can be misused to send commands to minions. The attacker will also be able to fetch the root key, which will provide him an unhindered connection to the master node.
2. CVE-2020-11652 Vulnerability Explained
This directory transversal flaw is related to the salt-wheel section, that stores different path folders for read/ write functions. The vulnerability was again created because of ‘ClearFuncs’, giving unsanitized access to attackers.
Effect: Allows to rewrite path elements, and gains unrestricted access to the master server’s complete filesystem.
The above two vulnerabilities are from different classes, but when combined, created a huge loophole in Salt’s framework, exposing and providing root access to any proficient cyberattacker.
In process of exploiting the above vulnerabilities, attackers had to follow the below simple steps:
- Connect to the ‘request server’ channel port
- This will help to bypass all authentication and authorization controls
- By publishing arbitrary control messages, the attacker can read and write files anywhere on the "master" server filesystem
- Then, steal the secret key which can be used to authenticate to the master as root
- The impact is full remote command execution access as a root user, on both the master and all minions that are connected to it
Real-World Impact of SaltStack Vulnerability
F-Secure’s team behind the discovery revealed that they initially identified over 6000 vulnerable Salt nodes on the web. The direct approach and simple nature of the flaws will allow any proficient hacker to create a fully-functioning, ready-to-use exploit in no time. And soon enough, after F-Secure’s announcement, many organizations have fallen prey to this trap.
- LineageOS - An open-source Android-based operating system
- Attack happened on May 2nd, 2020
- Read their full incident report here - Ghost - Node.JS blogging platform
- Attacker took charge on May 3rd, 2020
- Updates are being provided here - DataCert - TLS/SSL certificate providers
- System compromised on May 2nd, 2020
- Issue reported on Google Groups here
How to Fix SaltStack Salt RCE Vulnerability?
Luckily for everyone using Salt softwares, directly or indirectly through their customers, SaltStack had released the patch before the vulnerability was made public. If you’re still using previous versions, we suggest you hop on the patch train. To summarize:
SaltStack Salt Vulnerable Versions: <= 2019.2.0 and 3000
Updated Release: 2019.2.4 and 3000.2
For more information on how to secure your Salt systems click here, and on more information about the latest update, click here.


