Critical Bug in E-Learning LMS WordPress Plugins, Allowing Students to Cheat
A recent study has drawn attention to some critical bugs that will affect major e-learning platforms. CheckPoint, a cybersecurity firm has discovered severe vulnerabilities in 3 Wordpress LMS Plugins, namely LearnPress, LearnDash, LifterLMS

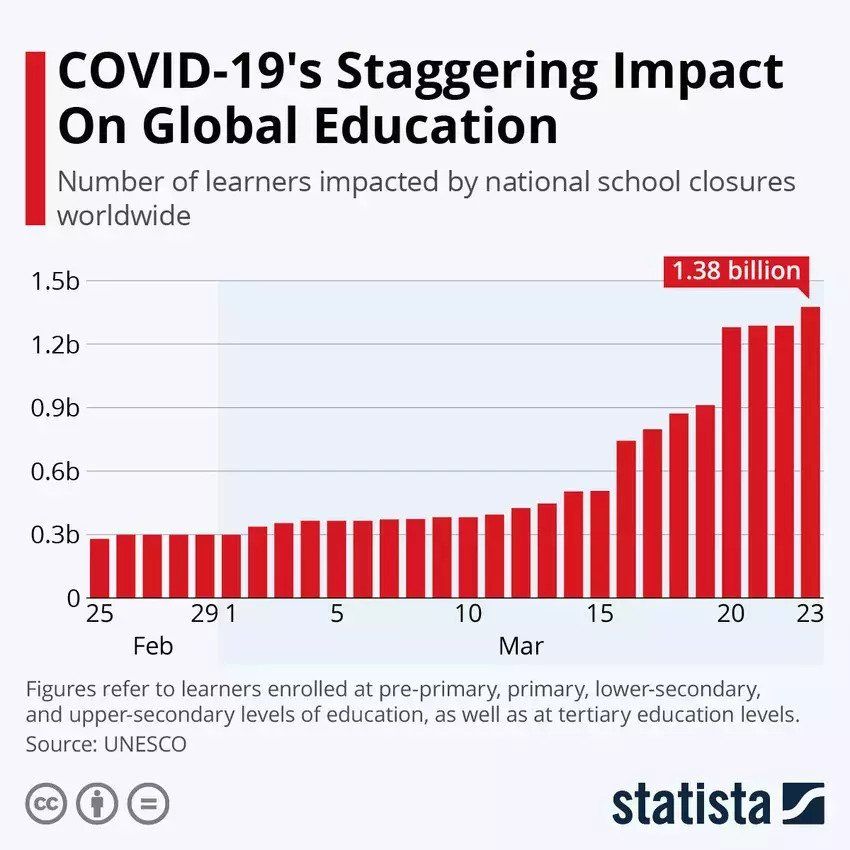
The COVID-19 global lockdown has not only affected businesses but also educational institutes, with an even larger number of student bodies to take care of. Though E-learning websites and applications have been in the market for a decade now, Coronavirus must take credit for their current viral status, as right now more than 1.3 billion students are studying from home.
Moreover, Learning Management Systems (LMS) are not just relevant right now; it is estimated that students grasp 40-60% quickly when studying online. Many schools and universities have already planned to go digital for the entire year. With such spotlight, e-learning platforms must gear up to prepare the blooming generation.
Amidst all this pressure, a recent study has drawn attention to some critical bugs that will affect major e-learning platforms. CheckPoint, a cybersecurity firm has discovered severe vulnerabilities in 3 Wordpress LMS Plugins, namely:
These plugins have been integrated in more than 130,000 educational websites, that include some major names like Universities of Washington, Michigan, Florida among other schools, academic institutions and even corporate organizations. These platforms serve a crucial role in online tutoring with quizzes & lessons, organizing and monitoring curriculum, coursework, student progress, test data and results. To give you the broader perspective of how dire this situation can be – Since their launch, these faulty plugins have been downloaded over 1.6 million times.
Now, Let’s dive in deep to discuss the technical side of these vulnerabilities and their real-world impact:
LearnPress: Bugs, Vulnerability & Exploits
Vulnerable versions: <= 3.2.6.7
Installed in: 80,000+ Websites
Mostly used in the United States, LearnPress LMS is the most famous plugin of the lot. But to everyone’s surprise, CheckPoint found major vulnerabilities here including:
- Time-based Blind SQL Injection (CVE-2020-6010), that manipulates the application by asking true/ false responses. The vulnerability is exploited the web app responds with generic error messages, and not the specific database errors.
- Privilege Escalation (CVE-2020-11511), or in this case ‘Becoming a Teacher’. This flaw lets a student call the associated function, and the code doesn’t validate the permissions of the requesting user.
LearnDash: Bugs, Vulnerability & Exploits
Vulnerable versions: < 3.1.6
Installed in: 33,000 Websites
LearnDash is one of the most high-profile E-Learning plugins that’s currently being used in Fortune 500 companies and leading US universities. It’s latest discovered flaw is:
- Another type of Unauthenticated SQL injection (CVE-2020-6009), that allows a non-registered user to trigger a fake enrollment process by taking advantage of Paypal’s IPN (Instant Payment Notification).
LifterLMS: Bugs, Vulnerability & Exploits
Vulnerable versions: < 3.37.15
Installed in: 17,000 Websites
LifterLMS is yet another leading LMS Wordpress plugin that has been popularized mostly amongst school academics. One of the most dangerous vulnerability of this research was found in here:
- Arbitrary File Write (CVE-2020-6008) lets the attacker upload a malicious PHP code in place of their profile picture, gaining full remote control of the e-learning system. This flaw is enabled because of improper validation during the file upload process.
LMS Hacked – Harmful Impact of E-Learning WordPress Bugs/ Vulnerabilities
These vulnerabilities might seem small put into words and alpha-numeric keys, but their real-world impact can be quite adverse. LearnPress, LearnDash and LifterLMS are some of the top names in the WordPress e-learning community. But the discovery of these major flaws has put a question mark on their code and security. These vulnerabilities allow students and strangers to access confidential information, and cheat in numerous ways. Let’s take a quick look at how can these plugins be manipulated through the above mentioned bugs:
- Stealing personal information data like username, name, email, phone number, address and even passwords.
- Changing own and fellow students’ grades,
- Gaining teacher access and privileges
- Forging educational certificates
- Retrieving the tests and answer keys beforehand
Additionally, put a professional cyber attacker in the mix with these loopholes, and the whole application data can be leaked.
How to Fix LearnPress, LearnDash, LifterLMS Bugs
The mentioned bugs were identified in March, 2020 and reported immediately to the concerned companies. All three LMS platforms have fixed and released the patch in their latest versions. So the most efficient way is to update your LMS and you should be good to go.
To read the full technical research paper from CheckPoint researchers Omri Herscovici and Sagi Tzadik, check out this link.


