The cyber security world is never at ease, always tossing and turning with a premonition of the next data breach, malware, exposed vulnerability or cybercrime news.
In the most recent uncovering of such cyber threats, NVIDIA has addressed multiple critical security vulnerabilities found in Windows and Linux machines. Earlier this month, Microsoft Windows also came under fire because of a critical SMB protocol vulnerability SMBBleedingGhost.
NVIDIA is immensely popular in the computer hardware space, for their impressive GPUs (Graphics Processing Units), designed and marketed for mainly the gaming industry. The company is a trusted manufacturer for all big players such as Microsoft, Dell, HP, Lenovo, etc, and in Windows and Linux devices for the most part.
This alarming news came in yesterday from official NVIDIA corporation sources citing 12 vulnerabilities, found in the GPU Display, CUDA Drivers and Virtual GPU Manager Software. They have been identified with proper CVEs (defined below), and assigned CVSSv3 scores ranging from 4.4 to 7.8.
NVIDIA Drivers – Windows & Linux Vulnerability
NVIDIA has warned and advised users around the globe about the high risk vulnerabilities present in Windows and Linux PCs. If compromised. a professional hacker can easily exploit your machine through local access. Once the local intrusion is achieved, the attacker can further exploit the target device by injecting malicious code remotely or through tools targeting these issues. Fortunately, gaining direct remote access is not allowed via these flaws, instead the attacker must get hold of your device first, to launch the following types of attacks:
- Denial of Service
- Privilege Escalation
- Code Execution
- Information Disclosure
Clearly these high severity issues can enable the threat actor to gain high privileges inside the operating system, where he can easily trigger denial-of-service attacks and compromise your entire device.
6 of the total 12 vulnerabilities have received high-risk assessment from NVIDIA itself in their June 2020 security updates. Let’s take a look at each of them individually.
NVIDIA Driver Vulnerabilities – CVEs and Explanation
NVIDIA GPU Display Driver
- CVE‑2020‑5962 - CVSSv3 Score: 7.8
NVIDIA GPU Display Driver contains a vulnerability in the NVIDIA Control Panel component, in which an attacker with local system access can corrupt a system file, which may lead to denial of service or escalation of privileges. - CVE‑2020‑5963 - CVSSv3 Score: 7.8
NVIDIA CUDA Driver contains a vulnerability in the Inter Process Communication APIs, in which improper access control may lead to code execution, denial of service, or information disclosure. - CVE‑2020‑5964 - CVSSv3 Score: 6.5
NVIDIA GPU Display Driver contains a vulnerability in the service host component, in which the application resources integrity check may be missed. Such an attack may lead to code execution, denial of service or information disclosure. - CVE‑2020‑5965 - CVSSv3 Score: 5.5
NVIDIA GPU Display Driver contains a vulnerability in the DirectX 11 user mode driver (nvwgf2um/x.dll), in which a specially crafted shader can cause an out of bounds access, leading to denial of service. - CVE‑2020‑5966 - CVSSv3 Score: 5.5
NVIDIA Windows GPU Display Driver contains a vulnerability in the kernel mode layer (nvlddmkm.sys) handler for DxgkDdiEscape, in which a NULL pointer is dereferenced, leading to denial of service or potential escalation of privileges. - CVE‑2020‑5967 - CVSSv3 Score: 5.5
NVIDIA Linux GPU Display Driver contains a vulnerability in the UVM driver, in which a race condition may lead to a denial of service.
NVIDIA vGPU Software
- CVE‑2020‑5968 - CVSSv3 Score: 7.8
NVIDIA Virtual GPU Manager contains a vulnerability in the vGPU plugin, in which the software does not restrict or incorrectly restricts operations within the boundaries of a resource that is accessed by using an index or pointer, such as memory or files, which may lead to code execution, denial of service, escalation of privileges, or information disclosure. - CVE‑2020‑5969 - CVSSv3 Score: 7.8
NVIDIA Virtual GPU Manager contains a vulnerability in the vGPU plugin, in which it validates a shared resource before using it, creating a race condition which may lead to denial of service or information disclosure. - CVE‑2020‑5970 - CVSSv3 Score: 7.8
NVIDIA Virtual GPU Manager contains a vulnerability in the vGPU plugin, in which an input data size is not validated, which may lead to tampering or denial of service. - CVE‑2020‑5971 - CVSSv3 Score: 7.8
NVIDIA Virtual GPU Manager contains a vulnerability in the vGPU plugin, in which the software reads from a buffer by using buffer access mechanisms such as indexes or pointers that reference memory locations after the targeted buffer, which may lead to code execution, denial of service, escalation of privileges, or information disclosure. - CVE‑2020‑5972 - CVSSv3 Score: 5.5
NVIDIA Virtual GPU Manager contains a vulnerability in the vGPU plugin, in which local pointer variables are not initialized and may be freed later, which may lead to tampering or denial of service. - CVE‑2020‑5973 - CVSSv3 Score: 4.4
NVIDIA Virtual GPU Manager and the guest drivers contain a vulnerability in vGPU plugin, in which there is the potential to execute privileged operations, which may lead to denial of service.
NVIDIA Drivers Patch and Fixes
As is standard procedure with such announcements, NVIDIA only reported vulnerabilities publicly after the respective patches have been released. In it’s security bulletin, the famous GPU company informed that,
“risk assessment is based on an average of risk across a diverse set of installed systems and may not represent the true risk of your local installation.”
Customers can find and download the patched NVIDIA Drivers from here.
Enterprises users will have to login to NVIDIA Enterprise Application Hub.
Additionally, NVIDIA has advised all users to update the following drivers and softwares:
- GeForce
- Quadro
- NVS
- Tesla
- vGPU Manager
- vGPU Guest Driver
You may want to check out the complete list of affected software products with their versions below:
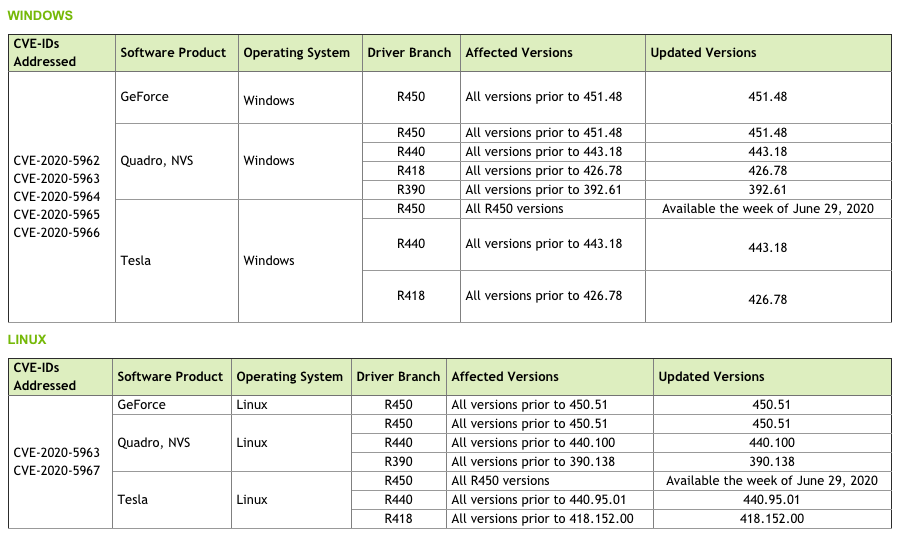
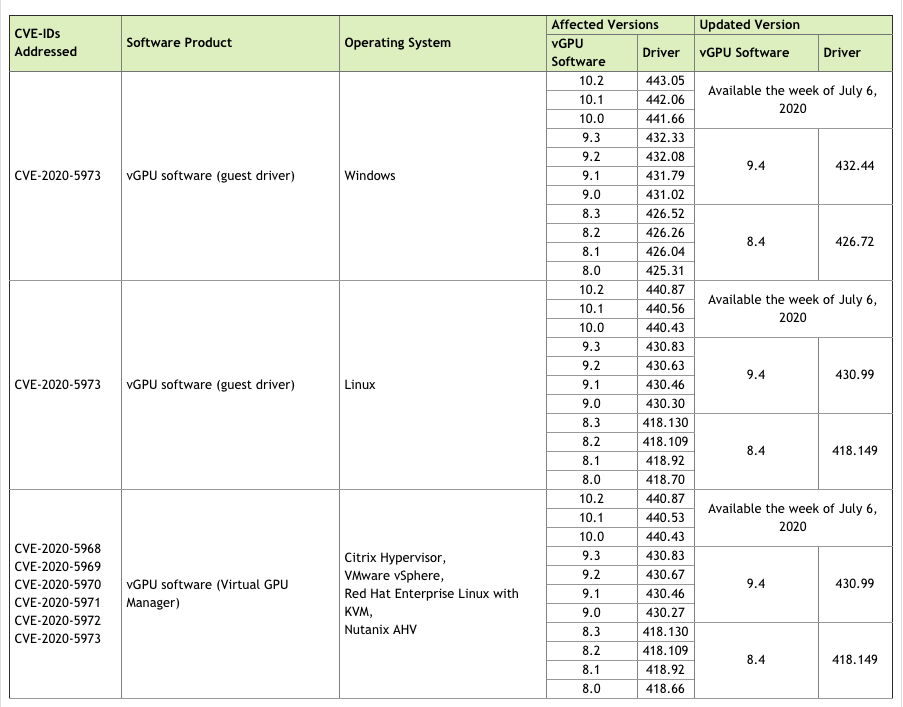
To find out which NVIDIA display driver version is installed in your machine, click here.
To read, NVIDIA’s June 2020 Security Bulletin, click here.
Follow us on Telegram and Twitter for all such latest cybersecurity news and updates.







