StrandHogg 2.0: Critical Android Bug Affects 1 Billion Smartphones; Allows App Hijacking
StrandHogg 2.0 malware exploits Android phones by allowing a malicious app to hide behind a legitimate app to trick the user. Thus, enabling threat actors to steal sensitive user information. Let’s learn more about the StrandHogg vulnerability.

Just a few months back in December 2019, the world was introduced to StrandHogg Android Vulnerability that lets a malicious app hijack your phone through Android’s multitasking feature. It worked quite simply:
- The malicious app (that exploits StrandHogg vulnerability) needs to be installed on the victim’s Android phone
- The victim clicks on any trusted app (including system apps)
- Instead the malicious app opens up, masqueraded with similar UI as the ‘clicked’ application
This interception allows the malware (or cyberattacker operating it) to acquire privilege credentials, banking details, etc. by showing fake login screens. Another threat that comes from this flaw is getting the user to grant important device permissions. To understand StranHogg 1.0 more clearly, take a look at the demonstration below:
StrandHogg 2.0 Malware
The Norwegein team of researchers from Promon, who discovered StrandHogg 1.0 vulnerability, have just revealed StrandHogg 2.0 - The Evil Twin. The name comes from a Norse term that means ‘hostile takeover’. They have debuted this bug with a scary introduction, stating that StrandHogg 2.0 is ‘more dangerous, more difficult to detect’ than its older brother.
StrandHogg 2.0 is a critically severe vulnerability, as identified by Google, and has been classified CVE-2020-0096. This flaw affects all Android-based phones, except the most latest version ‘Android Q’ (or Android 10). According to Google’s April 2020 statistics, less than 15-20% of the global market is using Android 10; which evidently confirms that over 1 billion Android mobile devices are currently exposed to the StrangHogg 2.0 exploit.
What is StrandHogg Bug? How is it Affecting 1 Billion Android Devices?
StrandHogg 2.0 is a privilege escalation bug that doesn’t require the root access or related permissions to be executed, and can also be executed without user interaction.
StrandHogg 2.0 adopts the reflection technique, and simply adapts the identity of other legitimate apps installed in the victim device. As soon as the StrandHogg malware application gets installed, the cyberattacker at backend will instantly be able to mimic all applications on the said device, without the need to pre-configure each target app.
After installation, all the user has to do is click on the app icon of any mobile application, and StrandHogg will immediately take its place and show a malicious screen (with the same interface). The victim, unknowingly, will provide device access or login details to the attacker, who can misuse these permissions and data to his like.
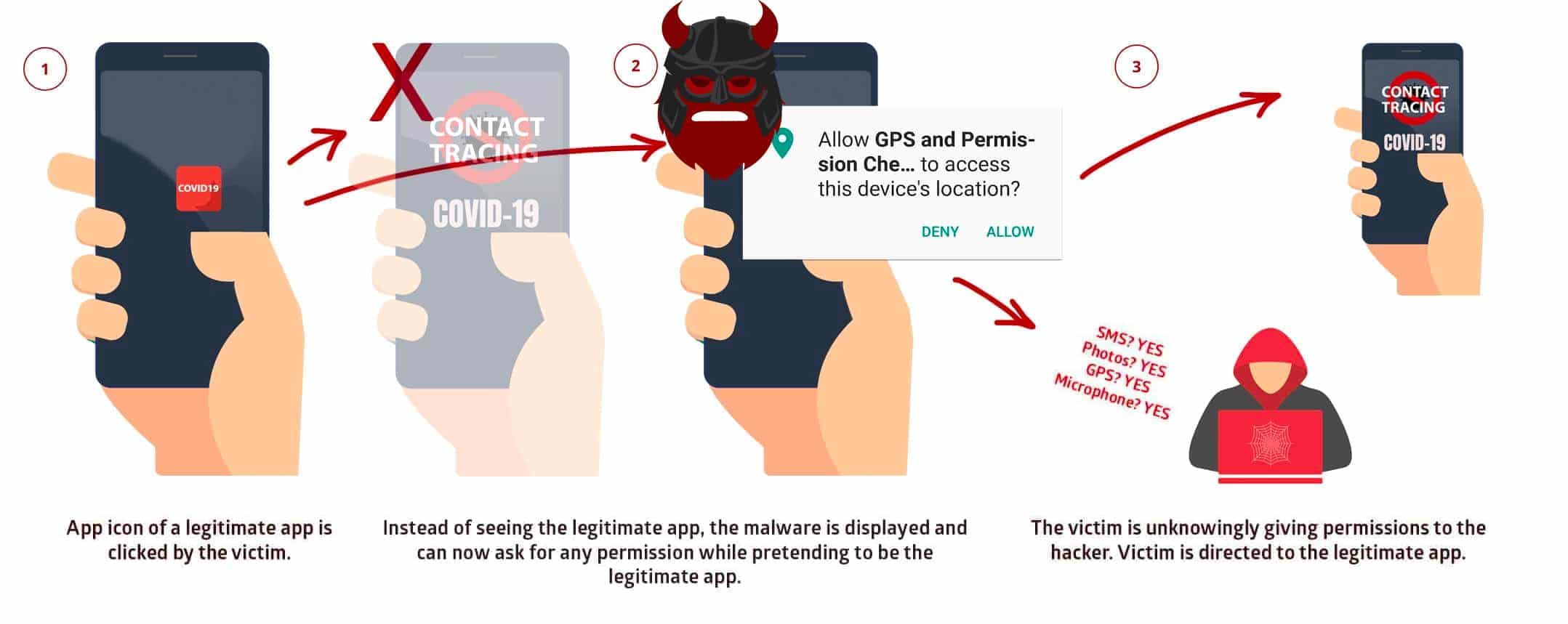
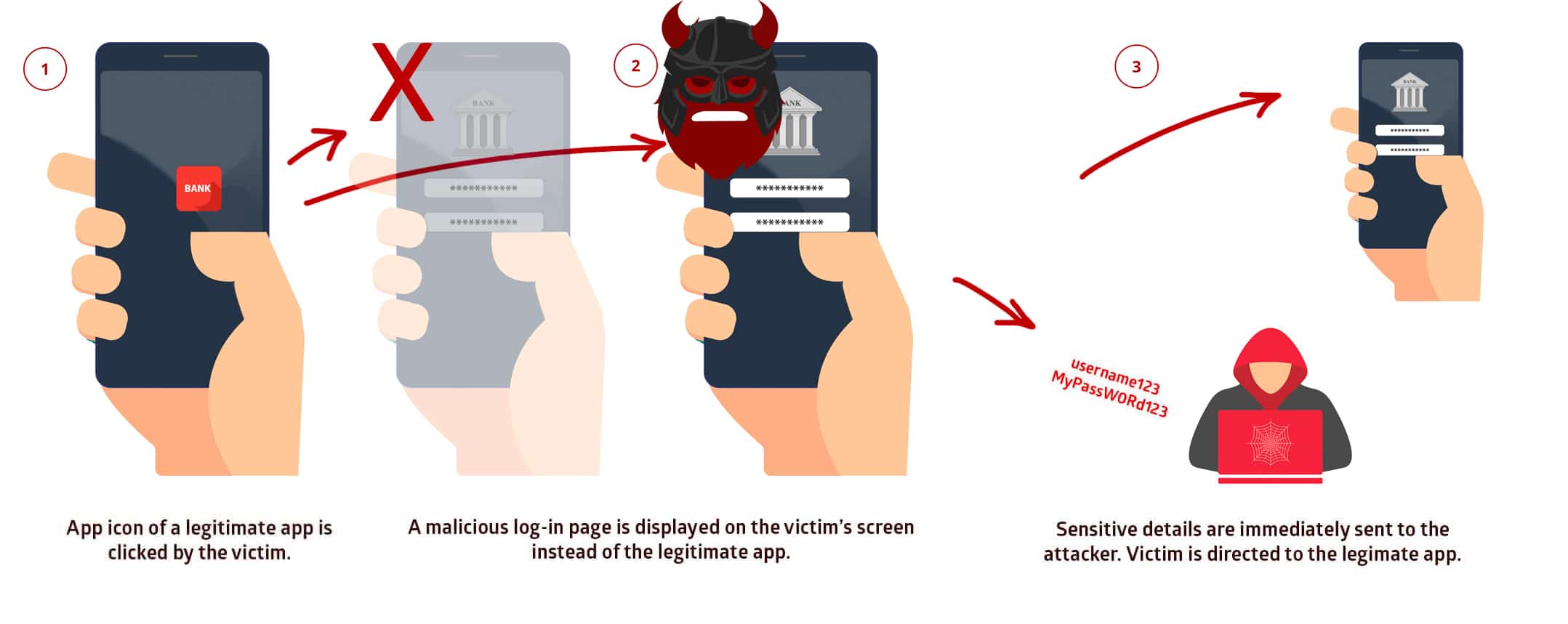
To summarize, exploiting Strandhogg 2.0 vulnerability will enable the attacker to access:
- Photos
- SMS Messages
- Login credentials of the target application
- Record phone calls and conversations
- Spy using the mobile’s microphone and camera
- Track user location via GPS
- And more
StrandHogg 2.0 vs StrandHogg 1.0
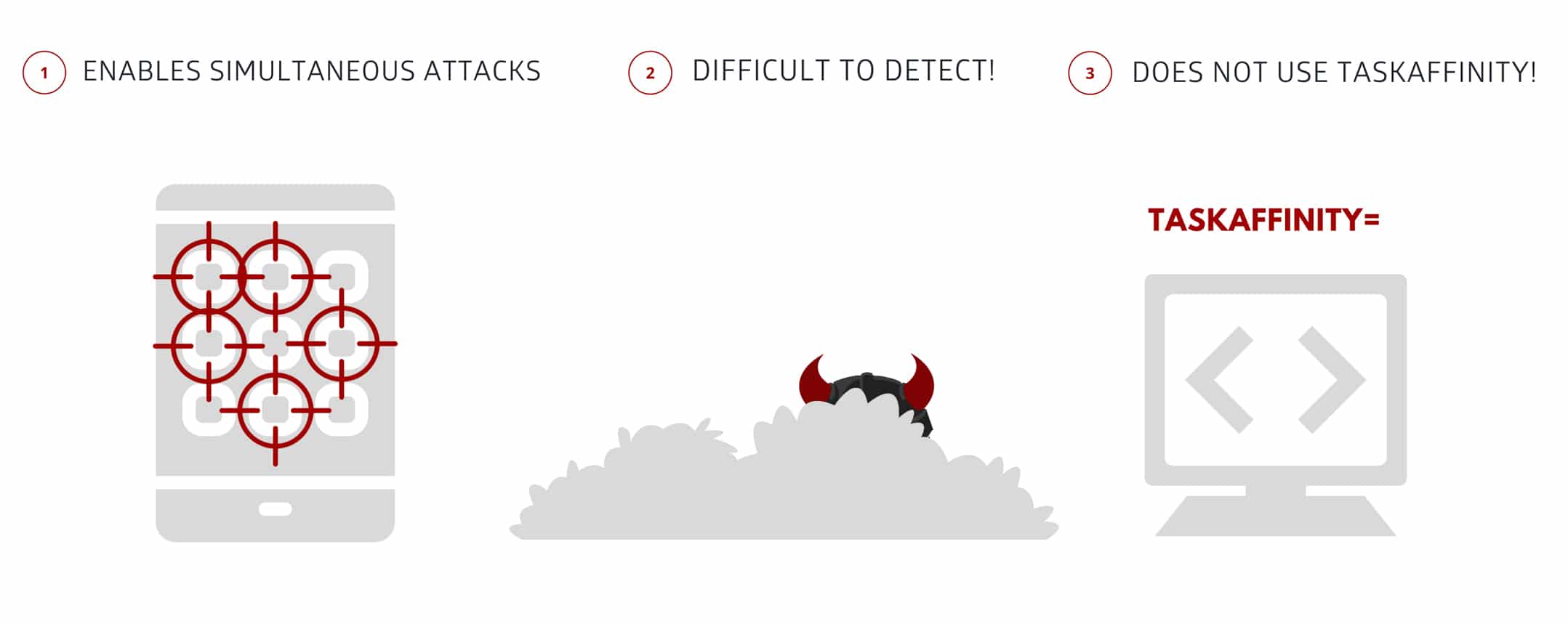
The latest StrandHogg vulnerability is similar yet different from the original. We can say that in some ways, it is an improvement (from a Cyberattacker POV). For example, unlike the first version, StrangHogg 2.0 doesn’t work around Android's ‘Task Affinity’ function.
In other words, StrandHogg 1.0 could only attack one app at a time, while StrandHogg 2.0 can perform dynamic attacks simultaneously on multiple or all apps on the infected device. This significantly augments the latter’s power and attack capabilities.
But the biggest threat posed by StrandHogg 2.0 is its sophisticated attack method that leaves no trace behind, and can easily trick security experts, scanners and anti-virus. This is achieved because of StrandHogg 2.0’s ‘code-based execution’ with no external configuration.
StrandHogg 2.0 Fix & Patch
Much to every Android user’s relief, Promon has stated that they haven’t found StrandHogg 2.0 to be the bad guy in any of the major hacking campaigns. The bug got discovered in December 2019, and the security researchers team immediately notified Google.
In April 2020, Google released the StrandHogg 2.0 Patch and started distributing it. The smartphone manufacturing companies will soon start delivering the relevant software updates for this flaw.
All we can do now is wait for our device’s next software release. Nevertheless, we should always follow cybersecurity best practices, and watch out for dubious activities like:
- Beware of any StrandHogg app download, by avoiding unheard of or suspicious applications
- Your frequently used apps don’t unexpectedly ask:
- You to Login
- Device Permissions - When the legitimate app’s buttons and links don’t work as expected
To read the full report from Promon, please click here.


