High Severity PageLayer Plugin Vulnerability Exposes 200K WordPress Sites to Wipe Attacks
2 Latest WordPress PageLayer Vulnerabilities allow hackers to wipe entire content from your website. Learn how they are doing it and how to fix PageLayer vulnerability.
WordPress is a user-friendly CMS, preferred and used by millions of businesses, bloggers and individuals around the world. It currently powers 35% of all websites on the internet. Even with such a wide reach, this mega-platform has been under cyber experts' radar for various security concerns. One of the most common attacks include hackers exploiting WordPress’ popular plugins.
PageLayer is a popular WordPress plugin that enables non-technical users to build their website by simple drag-and-drop features. It’s fairly easy to use and works with most WordPress themes available in the market. According to latest statistics, it is currently installed and actively used in over 200,000 websites.
On May 28, 2020, Wordfence, a WordPress security firm, disclosed 2 critical vulnerabilities that can let threat actors take over your PageLayer-installed WordPress website.
WordPress PageLayer Vulnerability: How it Works?
Wordfence explained that a cyberattacker can take advantage of the 2 new-found security flaws in PageLayer WordPress plugin to launch wipe and takeover attacks.
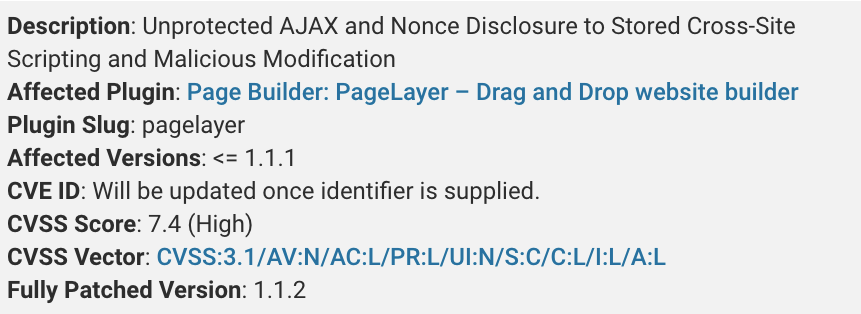
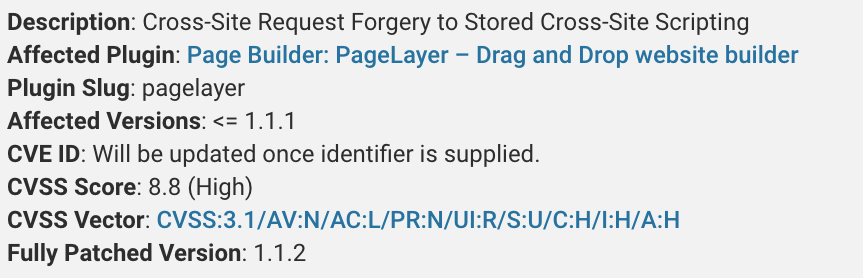
The first vulnerability allows a subscriber (or high-level) user to manipulate website posts’ content. While the second flaw took things to the next level by allowing a threat actor to fake an administrator-level request to alter plugin settings. This would further enable the attacker to inject malicious javascript into the site’s code. These PageLayer vulnerabilities occurred as a result of:
1. PageLayer’s exposed AJAX actions, which failed to validate permission checks. This indirectly gave access to any authenticated user to perform admin-level activities.
2. Another issue with PageLayer was nonce disclosure in the header’s page source . For those unaware, Nonce is simply a key in WordPress used to protect forms/ urls from hackers. By gaining this nonce, any site visitor can pose as a legitimate user to misguide AJAX actions, along with other security issues.

3. As Nonces can be easily compromised, they further impact CSRF (Cross Site Request Forgery) protection in WordPress.
The combination of above compromised functions gave birth to the 2 mentioned high-severity PageLayer vulnerabilities with CVE IDs yet to be identified.
The real-world impact of these vulnerabilities could be devastating to the site-owner as well as normal visitors. Some of the major repercussions might include:
- Creation of rogue user and administrator accounts
- Modify the website’s posts and pages
- Erasing or wiping out entire website and its contents
- Misleading the users and redirecting them to 3rd party malicious links
- Even the site visitor’s PC can be at risk as the hacker can compromise his security through the browser
PageLayer Patch
On April 30, 2020, the threat intelligence team at Wordfence disclosed the vulnerabilities to PageLayer’s development team, who soon released a patch in their latest version on May 6, 2020.
Previously Vulnerable Version: 1.1.2
Patched Version: 1.1.4
As of May 27, around 120,000 websites were still using PageLayer v1.1.2. If you’re working on a PageLayer WordPress website, please update your plugin immediately to forego any such risks and attacks. To read the full report from Wordfence, click here.


