New Zero-Day Psychic Paper Exploit Allows Access to your Entire iPhone
Siguza, an iOS researcher, recently reported a ‘Psychic Paper’ exploit where Cyberattackers can access your iPhone’s 100% private data including sensitive files, photos, messages, etc. by implementing Sandbox Escape exploit in malicious applications.

Another day, another iOS exploit discovered! There has been no shortage of iPhone hacking news, beating Apple’s strongly publicized system security. From camera, fingerprint to emails and messages, most of the iPhone's components have been exploited multiple times.
But the latest shocking revelation came on April 30th, 2020 from an active iOS hacker & researcher, with a knack for zero-day exploits – Siguza. In his latest blog, he disclosed his first 0-day exploit ‘Psychic Paper’ which he discovered around 3 years ago, and has since used for thousands of research projects.
RIP my very first 0day and absolute best sandbox escape ever:
— Siguza (@s1guza) April 29, 2020
<key>application-identifier</key>
<string>...</string>
<!---><!-->
<key>platform-application</key>
<true/>
<key>com .apple.private.security.no-container</key>
<true/>
<key>task_for_pid-allow</key>
<true/>
<!-- -->
Why the name? Well Siguza was inspired by Doctor Who’s magical ID of the same name. Much like the exploit, the ID had the super power to bypass any security check.
What is Psychic Paper Exploit? – Explained for Beginners & Experts
In this section, we’ll be breaking down Siguza's entire thesis in layman terms, so it's easier for anyone with basic workaround knowledge to understand. But before opening the book, let’s give you a little background (all terminology has been explained in relation to the ‘topic of discussion’):
- iOS and macOS use ‘plist’ or ‘property list’ XML-format files, for code signatures.
- Think of a Code Signature as a signature certificate that is provided to iOS applications
- There are 2 types of Code Signatures:
- Official AppStore Signatures: When the app is approved by iOS’s strict review standards.
- Developer Signatures: For IPA Apps (under-development applications). They are “placed in your App.ipa bundle at Payload/Your.app/embedded.mobileprovision. This file is signed by Apple themselves, and specifies the duration, the list of devices, and the developer accounts it is valid for, as well as all the restrictions that should apply to the app” explained in words of Siguza. - Sandbox is a specified set of resources provided to an application to run in. For example, Instagram has access to your images folder but nothing beyond that. System or sensitive information is usually restricted for safety purposes.
- Entitlements are a ‘set of privileges’ assigned for every application separately. They are written in the Code Signatures as plist files, and define Sandbox properties. They allow/ disallow the permissions of the given application within the iOS environment.
Now, to connect all the dots, Psychic Paper works by messing with the Entitlement plist files to access any sensitive data within the host iOS device. This process is known as Sandbox Escape. It works mainly with IPA Apps, as AppStore applications are carefully scrutinized for any such possibilities.
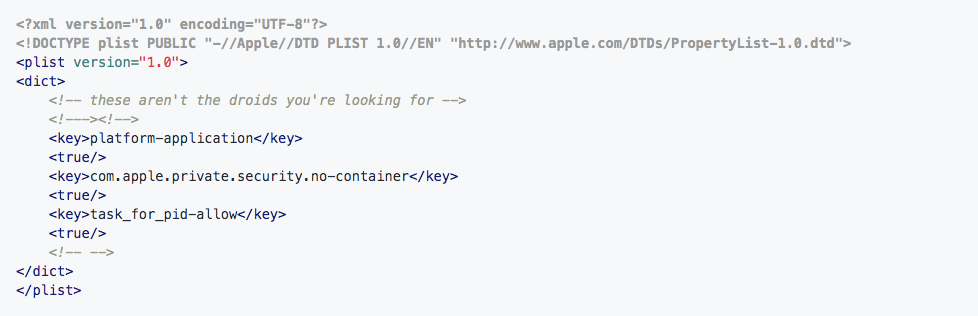
For his paper, Siguza demonstrated the Sandbox Escape with 3 malicious entitlements:
- com.apple.private.security.no-container: Used for completely destroying all iOS security parameters, by gaining access to read and write all files that the iPhone user has access to.
- task_for_pid-allow: This takes us a notch above, by viewing any process’s task port and allowing the attacker to read and write the process memory.
- platform-application: This masks any infiltration from non-Apple binary as a genuine agent, to gain access across “task ports of Apple binaries”.
Interestingly, the exploit was able to access everything except for 2 privileges, kernel and root (for obvious reasons).
If you want to get into Siguza’s geeky head and explore his complete technical process, we suggest you read his full blog article here.
Harmful Impacts of iPhone Psychic Paper Exploit
The real-world impact of Psychic Paper can be detrimental as it runs on not only iPhones, but the entire family including iPads, Mac, Watch and other Apple devices.
After reading about its ability to jump all security posts and hurdles, we can be sure of its devastating effects, if it falls into the wrong hands. Your victim iOS device will be completely vulnerable to the attacker, with no location barrier, as it can be accessed remotely.
Since the public announcement of this exploit, few other researchers have come out with their own experiments. One of them is Wojciech Regula who was able to ‘steal’ the SMS messages/ imessages with the sms.db file. Another interesting hack was created by Jan Kaiser who was able to gain shell access to the root file system with read/ write privilege.
Christmas came early thanks to Santa @s1guza 🎅🏻
— Jan Kaiser 🛡️ (@jankais3r) May 1, 2020
Combine @iSH_app with his sandbox escape 0day (https://t.co/r9HHo7Cetf) and you got yourself a shell with r/w access to the root fs. Almost as good as a jailbreak, in some aspects even better. pic.twitter.com/PQeUjwHddf
How to Fix Psychic Paper iOS/ iPhone Exploit?
The question is in the answer itself.
Think of why would Siguza come out with the exploit now, after hiding it under wraps for 3 years? Well, Apple just released its patch in the latest iOS 13.5 beta 3 update. This vulnerability (CVE-2020-3883) of arbitrary entitlements was credited to Linus Henze.

So as a final goodbye to his first-ever zero-day, he wrote a detailed article to offer a ‘Rest in Peace’ salutation.
New blog post: "Psychic Paper"
— Siguza (@s1guza) May 1, 2020
The story of the best. Sandbox escape. Ever.https://t.co/tIiT68Dcs3
To ensure your personal safety, don’t download any suspicious applications till you are using iOS 13.4.1 version, and make sure to download the latest update as soon it is made available.


